Azure Sentinel Overview
One of the biggest advantages of Microsoft’s Azure Sentinel SIEM is its seamless integration with Azure and Windows solutions, specifically Windows Defender, Microsoft Advanced Threat Protection (ATP) and Microsoft Cloud Security. While it is best
fit for current Microsoft Windows and Azure shops, its Microsoft-centric focus could make it less-suitable for organizations with multi-cloud and hybrid architectures. In this piece, we detail Azure Sentinel’s main feature sets and explains how best
to deploy them to monitor for threats and secure your workloads.
What Is Microsoft Azure Sentinel?
Sentinel is a scalable, cloud-native security information and event management (SIEM) and security orchestration, automation and response (SOAR) solution. It helps teams investigate threats with artificial intelligence (AI) and hunt for suspicious activities
at scale, tapping into years of cybersecurity work at Microsoft.
Sentinel is a best for organizations using Azure or those that are Microsoft-centric with a ton of Windows machines deployed. It’s often bundled with Office 365, so that's where it's really strong.
Getting Started with Azure Sentinel
To on-board Azure Sentinel, you first need to connect it to your security sources. Azure Sentinel comes with several out-of-the-box connectors for Microsoft solutions that provide real-time integration, including Microsoft Threat Protection and Microsoft
365 solutions, including Office 365, Azure AD, Azure ATP and Microsoft Cloud App Security, among others.
It also offers built-in connectors to the broader security ecosystem for non-Microsoft solutions (e.g., ServiceNow and Okta). However, customers can use common event format, Syslog or REST APIs to connect their data sources with Azure Sentinel, further
broadening its coverage.
READ: Enterprise Security Architecture Best Practices
Analytics
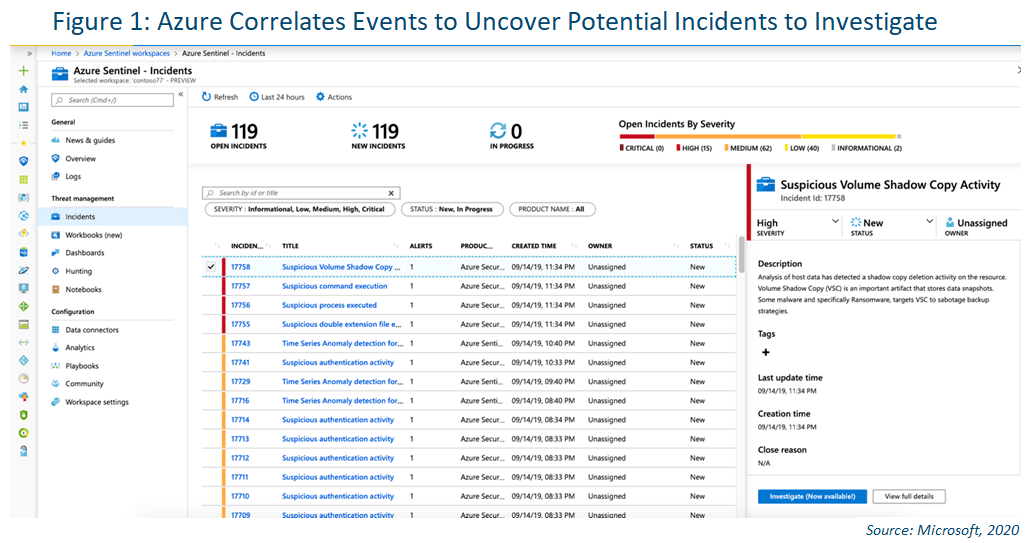
To help reduce noise and minimize the number of alerts to review and investigate, Azure Sentinel uses analytics to correlate alerts into incidents. Incidents are groups of related alerts that together create an actionable, potential threat to investigate
and resolve.
You can use the built-in correlation rules as-is or use them as a starting point to build your own. Azure Sentinel also provides machine learning rules to map your network behavior and then look for anomalies across your resources. These analytics connect
the dots by combining low-fidelity alerts about different entities into potential high-fidelity security incidents.
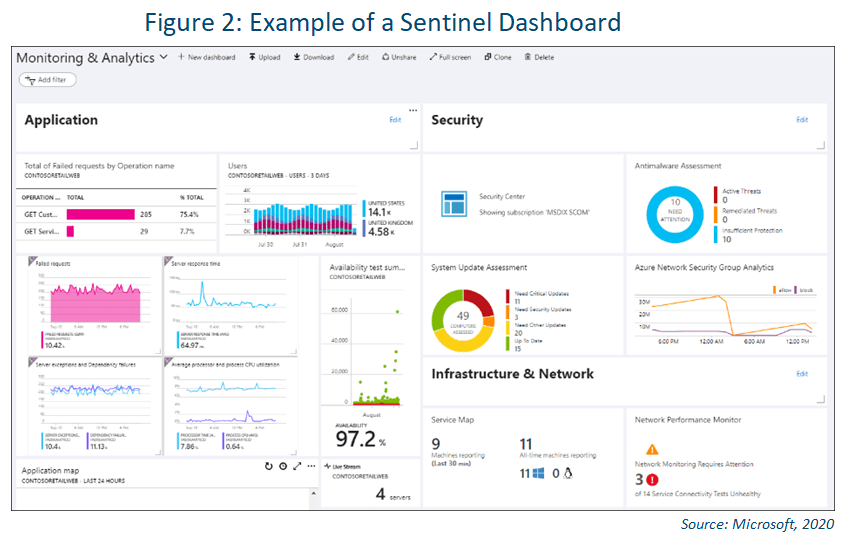
Dashboards
Azure Sentinel dashboards allow you to combine different kinds of data, including both metrics and logs, into a single pane in the Azure portal. You can optionally share the dashboard with other Azure users.
Elements throughout Azure Monitor can be added to an Azure dashboard in addition to the output of any log query or metrics chart. For example, you could create a dashboard that combines tiles that show a graph of metrics, a table of activity logs, a usage
chart from Application Insights, and the output of a log query.
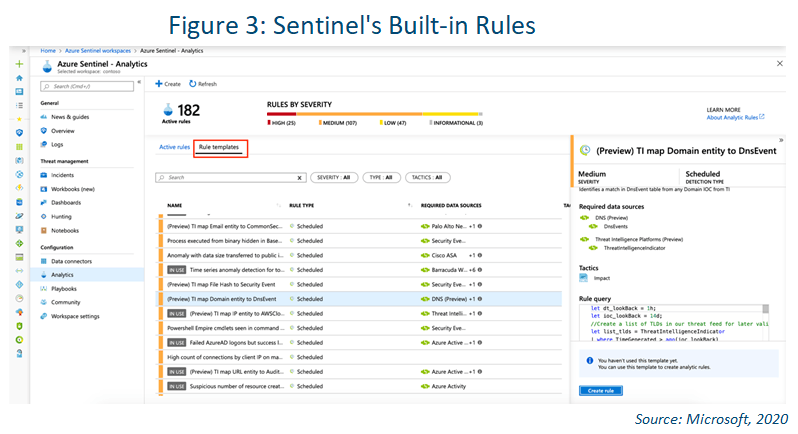
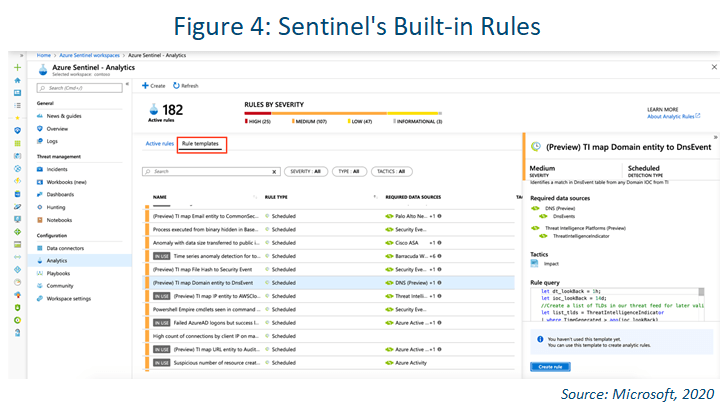
Detections
The following template types are available:
Microsoft security: Microsoft security templates automatically create Azure Sentinel incidents from the alerts generated in other Microsoft security solutions in real time. You can use Microsoft security rules as a template to create
new rules with similar logic. For more information about security rules, see this Microsoft documentation: Automatically create incidents from Microsoft security alerts.
Fusion: Sentinel’s Fusion is a technology that Microsoft says enables advanced multistage attack detection. It uses scalable machine learning algorithms that can correlate many low-fidelity alerts and events across multiple products
into high-fidelity and actionable incidents.
Machine learning behavioral analytics: These templates are based on proprietary Microsoft machine learning algorithms.
Scheduled: Scheduled analytic rules are scheduled queries written by Microsoft security experts. You can see the query logic and make changes to it, and you can use scheduled rules as a template to create new rules with similar logic.
Create New Detections
Sentinel also lets you generate detections on the data sources you connected to investigate threats in your organization. When you create a new detection, Sentinel lets you leverage the built-in detections crafted by Microsoft security researchers that
are tailored to the data sources you connected.
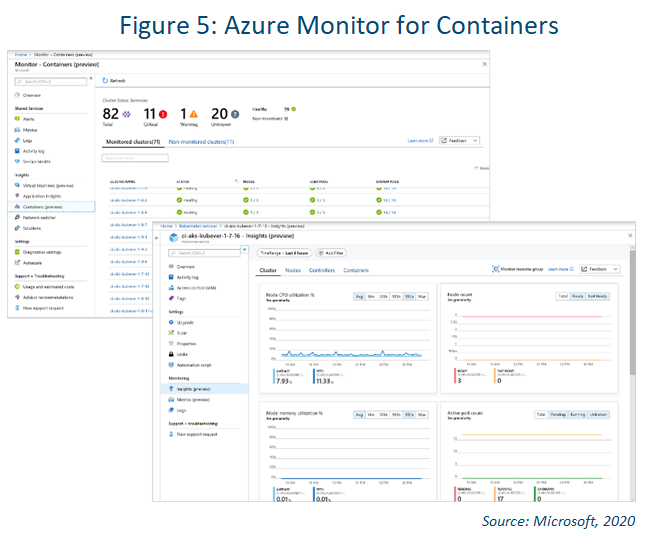
Monitor for Containers
Azure Monitor for containers is a feature designed to monitor the performance of container workloads deployed to managed Kubernetes clusters hosted on Azure Kubernetes Service (AKS). It provides performance visibility by collecting memory and processor
metrics from controllers, nodes and containers that are available in Kubernetes through the Metrics API. Container logs are also collected.
After you enable monitoring from Kubernetes clusters, these metrics and logs are automatically collected for you through a containerized version of the Log Analytics agent for Linux.
READ: Container Security Best Practices
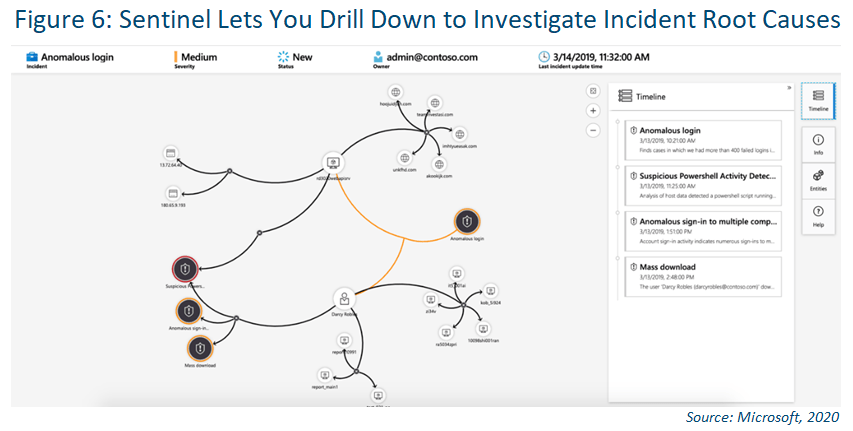
Investigation Tools
Azure Sentinel’s deep investigation tools reportedly help you understand the scope and find the root cause of potential security threats. You can choose an entity on the interactive graph to ask interesting questions and drill down into that entity
and its connections to get to the root cause of the threat.
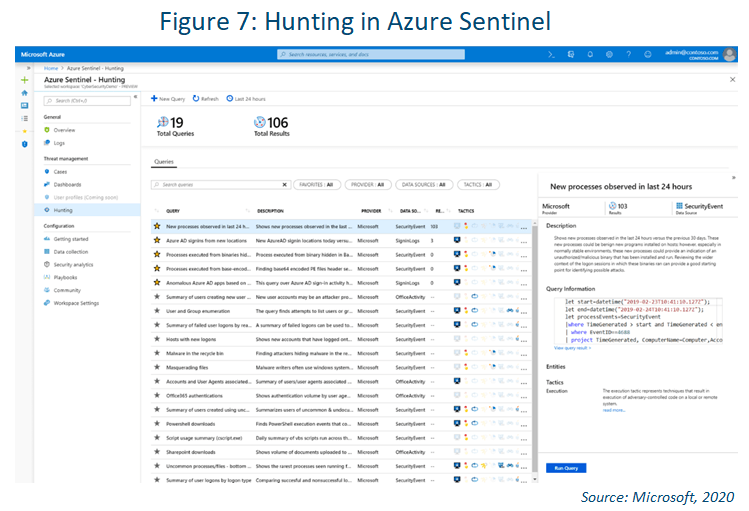
Hunting
Azure Sentinel's hunting search-and-query tools are stronger with Microsoft data sources, but are less optimal when working with non-Microsoft data. The tools are based on the MITRE framework. They enable you to proactively hunt for security threats across
your organization’s data sources, before an alert is triggered.
After you discover which hunting query provides high-value insights into possible attacks, you can also create custom detection rules based on your query and surface those insights as alerts to your security incident responders. While hunting, Sentinel
lets you create bookmarks for interesting events, enabling you to return to them later, share them with others and group them with other correlating events to create a compelling incident for investigation.
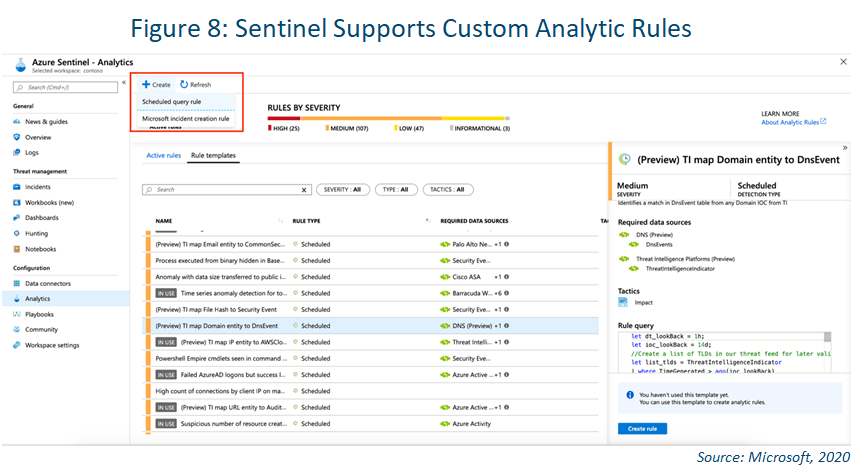
Custom Analytic Rules
Sentinel also lets you create custom analytic rules to help search for the types of threats and anomalies affecting your specific environment. The rules can be difficult to set up, but they provide immediate notifications so you can quickly triage, investigate
and remediate the threats.
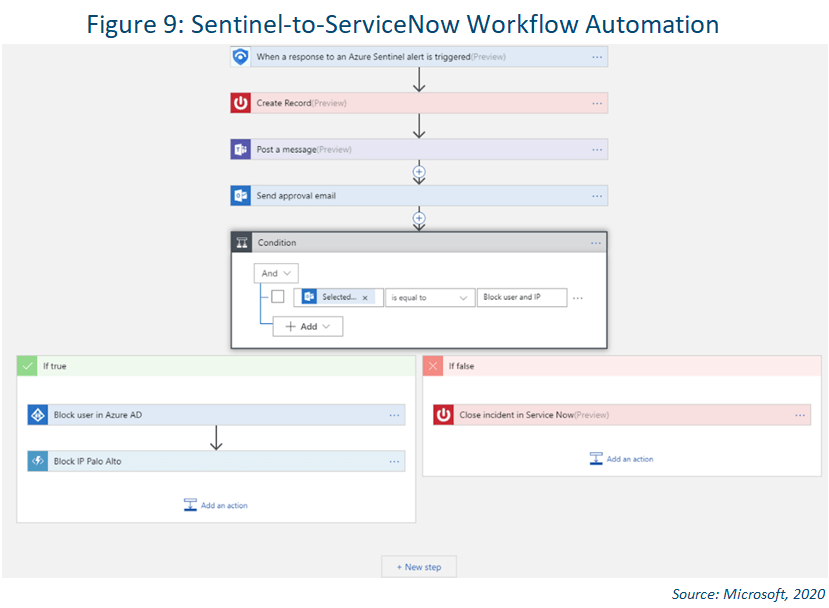
Security Automation and Orchestration with Playbooks
Sentinel also lets you automate your common tasks and simplify security orchestration with playbooks that integrate with Azure services as well as your existing tools. Built on the foundation of Azure Logic Apps, Azure Sentinel's automation and orchestration
solution provides a highly extensible architecture that enables scalable automation as new technologies and threats emerge.
You can choose from a growing gallery of built-in playbooks, including hundreds of connectors for a variety of Azure functions. The connectors allow you to apply any custom logic in code to support automation within services such as ServiceNow, Jira,
Zendesk, HTTP requests, Microsoft Teams, Slack, Windows Defender ATP and Cloud App Security. For example, if you use the ServiceNow ticketing system, you can use Azure Logic Apps to automate your workflows and open a ticket in ServiceNow each time
a particular event is detected.
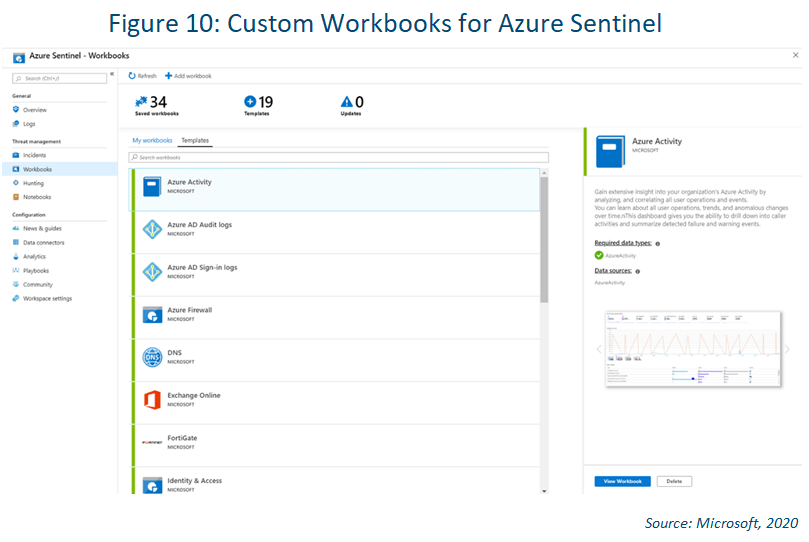
Monitor Workbooks
After you connect your data sources to Azure Sentinel, you can monitor the data using the Azure Sentinel integration with Azure Monitor Workbooks, which lets you create custom workbooks. While Workbooks are displayed differently in Azure Sentinel, it
may be useful for you to see how to create interactive reports with Azure Monitor Workbooks. Azure Sentinel allows you to create custom workbooks across your data, and also comes with built-in workbook templates to allow you to quickly gain insights
across your data as soon as you connect a data source.
Azure Sentinel Community
Microsoft-centric users will find the Azure Sentinel community a powerful resource for threat detection and automation. Microsoft’s security analysts constantly create and add new workbooks, playbooks, hunting queries and more, posting them to the
community for you to use in your environment. You can also download sample content from the private community GitHub repository to create custom workbooks, hunting queries, notebooks and playbooks for Azure Sentinel.
Outlook for Microsoft Azure Sentinel
Azure Sentinel is a viable SIEM solution if you are a big Microsoft and Azure shop. However, if you have multi-cloud workloads in AWS and GCP, you may struggle to collect and ingest data. We expect the product will improve and become an even strong player
in the SIEM space moving forward.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.