
Cloud Security: What to Expect in 2021
Cloud native security platforms (CNSPs) and the secure access service edge (SASE), both saw increased levels of investment from a combination of acquisitions and customer demand in 2020.
SASE saw the largest boost, thanks to stay-at-home orders due to the COVID-19 pandemic. Organizations that typically had 5 percent of their workforce remote, went to 95 percent in a week. Most found their aging remote access infrastructures simply could not scale to handle the demand, and SASE became the way to quickly scale, gain visibility and apply consistent controls, no matter the location of their users.
As information security teams move into 2021, we see new cloud security trends on the horizon fueled by a COVID-19-inspired cloud binge. In this piece, we bring you up to date on the current state of cloud threats, peer into what to expect from cloud security in 2021 and offer a structured approach for tackling cloud security in an ever-changing landscape.
Cloud Security Challenges for 2021
At the root of all cloud security challenges are two concerns:
- Securing access to the cloud.
- Securing workloads/data in the cloud.
SASE mostly addresses the first concern and CNSP mostly addresses the second. However, neither are a panacea for the underlying issue of cloud complexity.
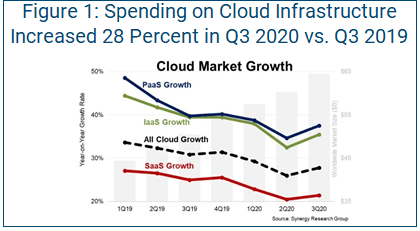
If you hoped cloud might go away, COVID-19 was your undoing. In a 2020 study conducted right at the beginning phases of the pandemic, enterprises reported being at nearly the halfway mark in their journey to the cloud. At the time of the report, organizations ran 46 percent of their workloads in the cloud and expected to get to 64 percent in the next two years (this was prior to the COVID-19 cloud surge). Consider the findings from Synergy Research Group that estimate enterprises spent $65 billion on cloud infrastructure services in the third quarter of 2020, an increase of 28 percent from the same quarter in 2019 (see Figure 1).
Complexity Equals Misconfigurations
This rapid uptick in demand for cloud services quickly led to increased security incidents, with 70 percent of enterprises running workloads in the cloud experiencing one, according to Sophos’ State of Cloud Security 2020 report. Why is this? Because we had cloud complexity and velocity without adequate automated process and controls across the development pipeline. The same report found cloud complexity and velocity led to 66 percent of organizations leaving services misconfigured, and misconfigurations lead to breaches.
Solving Challenges of Cloud Complexity
To solve the cloud complexity challenge, it is critical security programs holistically address both sides of the coin: securing access to the cloud and securing the workloads/data in the cloud.
Start the process by developing a one-page cloud security strategy. The problem set between these two areas of cloud security is very diverse. It is important to complete a gap analysis before jumping into technology and vendors. The gap analysis helps flesh out control gaps, as well as use and abuse cases. These can then in turn be used to drive vendor requirements and any resulting proofs of concept (PoCs) or proofs of value (PoVs) that might ensue.
Secure Access to the Cloud
This is about ensuring your user access resources both on-premises and in the cloud in a consistently secure manner. Here’s where SASE comes in. For the uninitiated, SASE represents the convergence of network-as-a-service and network security-as-a-service into one platform delivered from the cloud (not a hardware appliance). If you take the alphabet soup of firewalls, virtual private networks (VPNs), network data loss prevention (DLP), cloud access security brokers (CASBs), software-defined wide-area networking (SD-WAN), cloud secure web gateways (SWGs), etc., and deliver them all from the cloud, that’s SASE.
When approaching this side of the challenge, be mindful of impacts on other teams, such as networking. Because this is a convergence technology, part of your gap analysis should involve the development of a responsible-accountable-consulted-informed (RACI) matrix. This helps sort out who is going to own what and ensures your gap analysis includes feedback from key stakeholders. If you attempt to address security to the cloud without addressing this first, you may end up with a solution that meets the needs of one team while ignoring those of another. That can result in the realized value of SASE being far lower than anticipated, due to point products needing to be brought in later, or the lifespan of costly legacy products being extended to fill the gaps.
SASE Vendors
Palo Alto Networks Prisma Access and Zscaler Internet Access (ZIA) are top-of-mind in the market. Innovation has mainly come in the form of acquisitions. In 2020, Palo Alto acquired SD-WAN provider CloudGenix and Zscaler broadened its appeal by acquiring Cloudneeti, a cloud security posture management (CSPM) company focused on infrastructure- and platform-as-a-service (IaaS/PaaS) security. A newer entrant to the space is Netskope.
When choosing among SASE vendors, organizations should:
- Consider existing investments with each. Do you already own any of their products? If so, it should have a leg up in your decision-making process.
- Focus on your gaps and use/abuse cases. Focus on your use/abuse cases and gaps, while executing a PoC/PoV with your top two choices. Be sure to dig into granular details, such as which protocols you need to support. Historically, Zscaler is based on proxy technology that does well with HTTP, HTTPS, FTP and DNS protocols. Prisma Access, on the other hand, is based on next-generation firewall (NGFW) technology, which often supports a broader range of protocols. The devil is always in the details, so be sure you document your protocol requirements completely.
Secure Data/Workloads in the Cloud
This is where automation and development pipelines come into clearer focus (although this is less so with SaaS since the provider manages the code base and you as the customer are left largely managing configurations and identity permissions). Complexity is perhaps at its greatest with IaaS/PaaS, since customers must do the heaviest lifting. In fact, complexity has risen to the point where industry groups such as the Open Networking User Group are pressuring cloud providers to standardize how they handle security.
As before, it is critical to complete a RACI. In all three cloud models, you as the customer are giving up differing levels of control, but never accountability. The RACI is important because the responsibility for security is likely going to be split across multiple different teams including networking, security, DevOps and IT.
When approaching this problem set, consider splitting it into two separate domains:
- With IaaS/PaaS, you need to secure the entire development pipeline and the ability to perform massive amounts of automation.
- With SaaS, the challenges you need to solve will be largely limited to configurations, data and identity. These three exist in IaaS/PaaS too, but you also must account for infrastructure and development components.
CNSP Vendors
Two vendors in the CNSP space include CloudGuard from Check Point, Aqua Security and Prisma Cloud from Palo Alto Networks. To make a product decision, as before, start by looking at what you already own. You may already have Check Point or Palo Alto gear in your environment. Investigate how you might be able to leverage existing enterprise license agreements (ELAs) to get competitive on costs. While cost should not be your primary driver in product selection, reduced complexity should be.
When looking to secure IaaS/PaaS platforms, be sure to include the configuration of the cloud itself as well as the workloads and data running inside it.
When evaluating CNSP vendors, it’s also important to focus on:
- Use cases. Are containers and Kubernetes widely used in your organization? If so, look deeply into the providers’ workload capabilities during your PoCs/PoVs. This should include both vulnerability management and runtime security. Check Point is strong on the CSPM portion, but it has lagged both Prisma Cloud and Aqua Security on the workload protection component.
- Identity configurations. This is another area that came into sharp focus in the second half of 2020. Organizations need to secure identity configurations in cloud platforms such as Amazon Web Services (AWS), Microsoft Azure and Google Cloud. Research from Palo Alto’s Unit 42 finds 75 percent of organizations in Japan and Asia-Pacific (JAPAC), as well as 74 percent of organizations in Europe, the Middle East and Africa (EMEA), are using Google Cloud to run workloads with admin privileges. Identity has evolved to become the forefront of cloud security. When evaluating the above security providers, be sure to examine how they address proactively identifying and remediating common identity-related misconfigurations.
- Development pipeline. The other area to keep in mind is how well each product integrates with your development pipeline. This is an area of differentiation that requires you to work closely with your DevOps team to identify its toolsets and ensure out-of-the-box support. Aqua Security and Prisma Cloud are especially strong in these areas. As DevOps teams increasingly rely on infrastructure-as-code (IaC) templates to rapidly deploy and configure cloud environments, it becomes critical to also scan these templates for common misconfigurations. In a separate report, Unit 42 researchers note half of CloudFormation templates contain vulnerable configurations, and 22 percent of Terraform files contain at least one insecure configuration. Movement toward IaC and automation also spurred a new crop of startups in 2020, such as Accurics and Bridgecrew. While the larger vendors already play in this niche space, if these highly agile startups can prove a 10x advantage, they could be ripe targets for a possible acquisition.
SaaS Security and SSPM
A new market that emerged in 2020 was SaaS security posture management or SSPM. This new crew of startups (e.g., AppOmni, Obsidian and Adaptive Shield) aim to secure the configuration of popular SaaS platforms such as Microsoft 365, Salesforce and Box, to name a few.
SaaS security issues run the gamut from failure to enable multifactor authentication (MFA) to overly permissive sharing for external users. This new group of companies takes an API-based approach (no agents, because that is not possible with SaaS) to add visibility and remediation into the configuration of SaaS platforms.
Due to the early nature of this market and overlap with some existing CASB capabilities, we expect to see some consolidation in 2021.
SASE and Cloud Native
As we peer into 2021, the current trends will continue to intensify. The shift to cloud is only going to increase. COVID-19 has assured this, with a combination of work-from-home for the foreseeable future (a widely available vaccine will bring some back to work, but it will not go back to what it was) and data centers continuing to go by the wayside.
In the SASE space, expect to see new players emerge, but rather the existing players will continue to augment their positions with smaller acquisitions and expanded capabilities, such as DLP.
In the CNSP (IaaS/PaaS) space, expect further consolidation via acquisitions and the smallest of players dying on the vine. When it comes to securing IaC, the market is still very young, and some current players already have capabilities in this area.
In the SSPM space, while it is still very new, SSPM vendors will seek to differentiate themselves in two ways: the number of SaaS platforms they support and the depth of capabilities in each.
Cloud Security in 2021
Innovation brings complexity, and this is precisely why the cloud security market is so fragmented. Despite cloud being around for over a decade, in the world of computing, it is still very new and changing rapidly. A general best practice for cloud security is to try and be as proactive as possible.
Develop a one-page cloud security strategy. This is not a technical document, but rather a casting of your vision of what cloud security means in your organization. Be sure to include people, process and technology.
Become the cloud champion. If your organization is one of the laggards that has yet to make a major move, you as the security practitioner are in a unique position. You can get ahead of the business to help it stay competitive. Work closely with the CIO to get a fix on when the move to cloud is coming. Even if the dates are murky, take the time to carve out a project that will create security guardrails in each of the major cloud providers. Doing this now will save major headaches later, and CNSPs will aid greatly in this effort.
Get SASE. If you managed to get through the pandemic with your aging remote access infrastructure, good for you. 2021 is the year to deeply assess potential cost savings as well as reduced operational complexity when it comes to managing multiple different sets of technologies such as SWG, CASB and SD-WAN. SASE is your path to doing this, while enabling you to apply consistent security controls no matter the location of your users.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.