
How to Establish an Effective Insider Threat Program
Insider threat programs are inherently difficult to build and maintain. Unlike other cybersecurity programs that focus on securing organizations from external threats, insider threat programs pit the organization against one of its own. This requires a fundamental shift in how cases are investigated, and the remediation actions taken to mitigate or eliminate the insider threat.
Attempting to take the same approach with insider threats as with external adversaries could potentially result in distrust in the security organization, low employee morale, and in some cases, civil liability.
In this piece we detail the roles and responsibilities required for an effective insider threat program, an example of workflow for insider threat investigations and some common mistakes to avoid.
Insider Threat Programs
A successful insider threat group incorporates key resources from across the organization. Because an insider threat program requires resources from multiple departments/business units throughout the organization, the charter to create a program usually comes from the chief risk officer (CRO), or delegate in a similar role.
Some information security organizations attempt to create a program unilaterally. And while information security teams may possess the technical means to deploy an insider threat program, organizations should consider involving HR and the general counsel in the investigation. (see Figure 1).
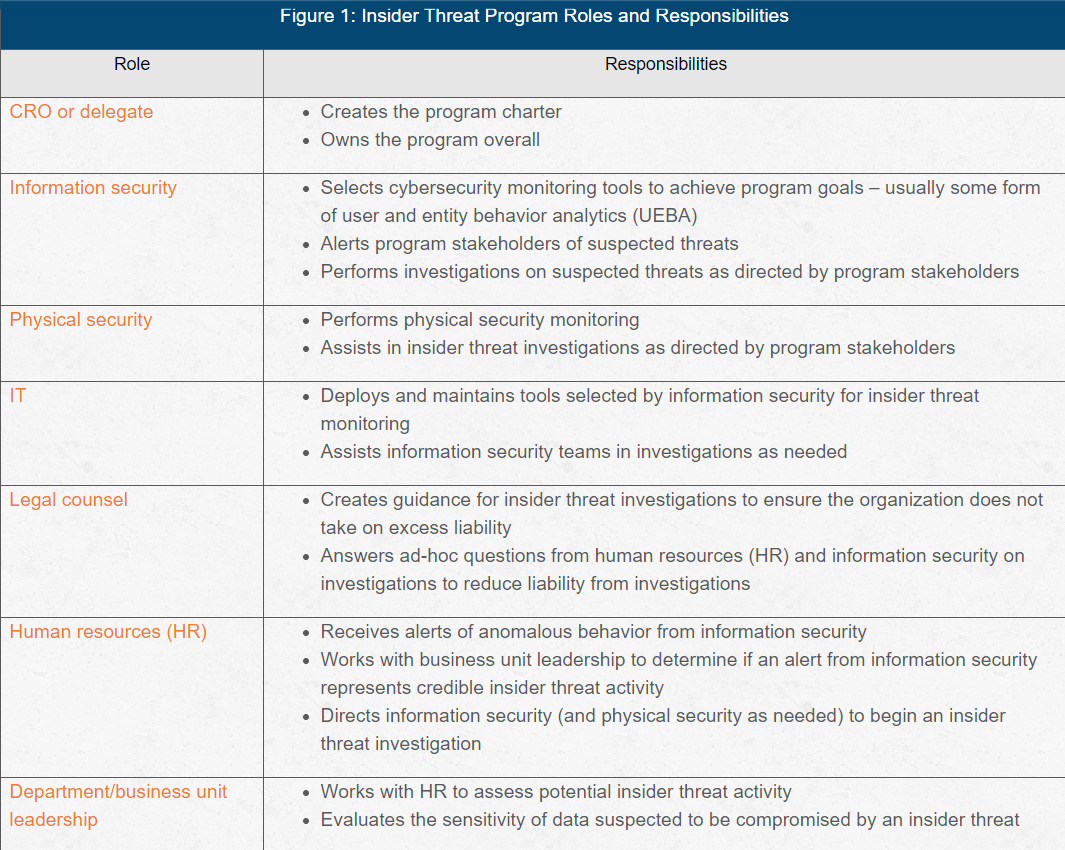
Consider assigning an incident handler to coordinate the different portions of the investigation.
In some cybersecurity incidents, the information security team provides the incident handler (this role is also sometimes referred to as "incident commander"). However, insider threat investigations differ in how they are investigated due to the liability that can emerge, and HR can provide the incident handler to direct investigation activities.
In some organizations, business unit leadership from the impacted division provides the incident handler, but this has the potential to shirt too much focus on protecting the value of the assets compromised by the insider threat, rather than minimizing the liability of an insider threat investigation. This instance can be avoided or at least minimized when and if HR directing all activities.
Insider Threat Investigation Workflow Example
The following is an example workflow for an insider threat case:
- Information security receives an alert in the UEBA system and determines that it does not appear to be a false positive.
- Information security reports the alert to an HR delegate on the insider threat team.
- HR works with business unit leadership detailed to the insider threat team to validate whether the activity discovered represents a credible threat or at least a credible reason to continue an investigation.
- HR directs information security to continue the investigation under the procedures outlined by the general counsel.
- The general counsel answers questions from information security about the guidelines for the investigation.
- Physical security representatives are engaged as a witness any time a device must be retrieved from a user's workspace.
- Information security reports technical findings to HR.
- HR works with the general counsel, CRO and union representatives (as applicable) to dismiss the findings of the investigation, reprimand the suspect or terminate the suspect’s employment.
It is not uncommon for many other steps to occur in the background which are detailed here in this simplified example for illustrative purposes. However, these can involve coordination between the general counsel and HR, or HR and business unit leadership, and are outside the purview of information security.
Insider Threat Program Mistakes
Mishaps in implementing insider threat programs can be innumerable, and therefore the following considerations should be taken as general guidance, rather than seen as complete or comprehensive. However, common mistakes made in insider threat programs include:
- Allowing information security to drive an investigation. All investigation parameters (what is searched, how it is searched, the scope of the investigation, etc.) should be dictated by HR, as developed with input from the general counsel and labor representatives. It is recommended that InfoSec teams obtain specific guidance from HR about any monitoring and investigative actions performed for insider threats.
- Not ensuring need-to-know for information sharing. Be aware an insider threat investigation could have the potential to create liability for an organization when information about a suspect is leaked outside the program. Participants should be made to sign additional non-disclosure agreements (NDAs) acknowledging their duty to keep information strictly within the group and only involve outside parties with permission from the CRO (or delegate). NDA violations within the insider threat group must be met with swift enforcement.
Often overlooked, insider threats can be even more dangerous than external threats. However, they must be addressed differently to minimize liability. Without sufficient process and oversight, an insider threat investigation could potentially result an increase in overall risk to the organization.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.