
Design a Successful Vulnerability Management Program
A 90-Day Guide for InfoSec Teams
Before jumping into the ways you can improve your vulnerability management program, it's important to build the big picture of the organization and establishing a solid foundation before getting lost in scan results and other weeds. This piece details key steps existing InfoSec teams or new information security managers should take to set your vulnerability management program up for success.
First Steps of Vulnerability Management
For years, vulnerability scanners competed in a race trying to be the vendor with the most vulnerability checks. This has led us to a situation where the results of a scan will nearly always be more than any organization could ever manage or remediate.
The first task is to get the lay of the land and understand the scope of the organization’s assets. Asset discovery and management are essential to vulnerability management because you can’t assess the state or risk of an asset until you know
what you have. This is a big undertaking, so try slicing it into more manageable pieces:
- Find assets and discover primary asset locations and categories.
- Identify asset owners.
- Form a vulnerability data gathering strategy.
Once that’s done, you can start to establish baselines, and create workable standards, procedures and metrics.
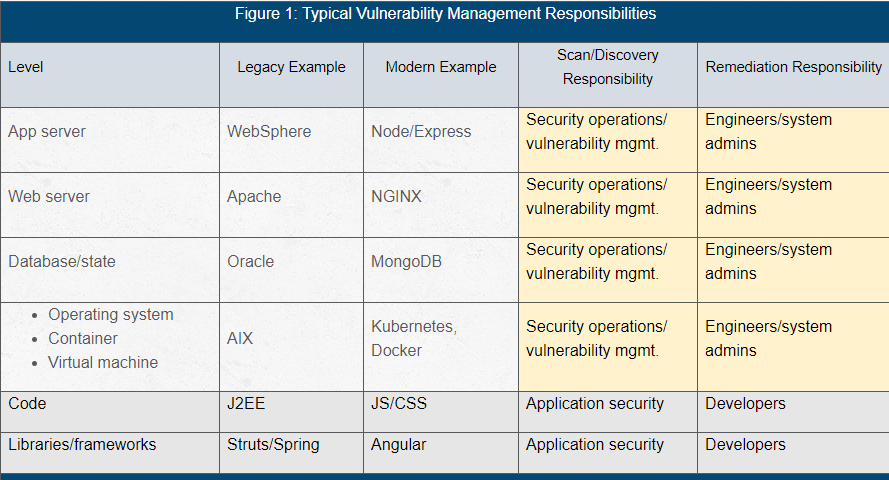
Please note: This discussion excludes application security vulnerabilities, because those are typically handled by separate tooling and teams in most organizations (but not all). Figure 1 shows how responsibilities tend to be separated out in most organizations.
Figure 1: Typical Vulnerability Management Responsibilities
First 30-Days: Getting Started with Vulnerability Management
1. Find the Assets and Categorize Them
Assets can be categorized in many ways, which can help with vulnerability prioritization, setting asset criticality and overall risk analysis. Example categories include by purpose, location, etc.
2. Find the Asset Owners
It's the InfoSec team's job to identify security issues and bring them to peoples' attention, but in almost every case, someone else will be responsible for fixing them. As early as possible, identify key contacts you can work with to get security issues
fixed. This should include (but probably won't be limited to):
IT, including:
- Key system administrators/engineers (folks that manage servers, workstations and/or cloud instances)
- AppSec
- Service desk/helpdesk
- DevOps engineers/cloud engineers
Disaster recovery (DR). You don't want your first task on the first day of a disaster to be dealing with a delay in switching over because DR systems are two years behind on patches. Most organizations of this size go high availability (HA) or hot/hot
for DR these days, so this might not be a concern, but it's always worth checking.
Marketing: Typically, marketing will own some of its own hosted or software-as-a-service (SaaS) infrastructure. It's extremely visible and shouldn't be overlooked.
Miscellaneous: It’s possible other groups own their own infrastructure or SaaS as well. Human resources (HR), legal and finance are all worth an exploratory look. It might be worth setting up a short 20-minute interview with each group to get a
better understanding of what software they use to get the job done. From there, you can often trace the software back to SaaS/infrastructure and figure out who the asset owners are.
3. Understand the Process
Once you find the asset owners, get an understanding for the current change management and patching/remediation process. Is there one company-wide process that's closely followed? Does each team fend for itself? Is there no change management at all? Are
patch management systems integrated into vulnerability management systems?
It’s important to understand current expectations and time constraints.
READ: How to Formalize Your Vulnerability Management Program
First 60 Days: Gather Vulnerability Data
1. Choose Your Data Sources
A major source for vulnerability information will likely be a vulnerability scanner or management platform.
A common pitfall is to treat the vulnerability scanner as the sole source for vulnerability data. Asset owners will often trust the criticality set by the patch management system or the vendor over the score the vulnerability scanner assigns.
Vulnerability data sources could include:
- Vulnerability scanners
- Vulnerability notification services
- Patch management services
- Bug bounties or vulnerability disclosures from third parties.
- Other good sources of data to improve the process include:
- Configuration management databases (CMDBs).
- Asset discovery and management tools, which should directly drive the vulnerability scanner targets.
Having a vulnerability disclosure policy (VDP). A VDP aims to make it easy for researchers or good Samaritans to quickly report security issues to an organization.
2. Decide How to Gather the Data
In addition to the sources of vulnerabilities, it’s also important to consider how the vulnerability data is gathered. This data can be gathered in a variety of ways, each with pros and cons. Take a hard look at how vulnerability data is currently
gathered and consider whether it is the best approach for the size and type of environment. Typical approaches include:
Network scanning. This is a point-in-time method that’s highly susceptible to changing network conditions, and whether assets are online or offline at the time of the scan. Scans often “get stuck” and some tools will automatically cancel
network scans if they don’t complete in 24 hours, without alerting you to the fact they gave up mid-scan. Network scanning is also the most likely method to produce false positives.
Credentialed scans. These are more accurate and reliable, but return much more data (most of it of a lower criticality and importance).
Agent-based scans. These are similar in completeness and quality to credentialed scans, but they require the additional inconvenience of rolling out agents to systems and maintaining the health of those agents. Agents are typically only compatible with
popular workstation and server operating systems, so network scans are still required to analyze network, internet of things (IoT) and other types of devices.
First 90 Days: Establish Vulnerability Baselines & Standards
1. Establish Baselines and Identify Anomalies
The key to identifying anomalies is establishing a baseline. Some anomalies are easier for humans to spot, while others can be spotted with automated reports or checks
2. Establish Custom Standards, Procedures and Metrics
Work to establish:
- Service-level agreements (SLAs): How long is the business comfortable letting a critical vulnerability exist before patching? What about a cluster of high-but-not-quite-critical vulnerabilities? Work with key asset owners and management to establish
SLAs for patching/fixing vulnerabilities that everyone can live with and that make sense, given the current state of attacks and breaches. In other words, if cyber threat intelligence (CTI) indicates attackers are actively exploiting a vulnerability, you
don’t have days or weeks to fix it. Modern InfoSec programs aim to address critical vulnerabilities in hours, not days or weeks.
- Standards: Set agreed-on timeframes for remediating a security issue based on criticality and other criteria.
- Procedures: Create agreed-on processes for gathering vulnerability data and acting on it. This should include mitigations for situations where patches can’t be installed temporarily or permanently.
- Metrics: Create metrics for how closely the standards are met to provide performance and trending data. They should be reported in plain English to management and executives. For example, you could say: “20 percent of critical restaurant systems
were exposed to actively targeted vulnerabilities for eight days this month.” Also, make expectations and goals clear when reporting metrics. The goal should never be to push risk to zero, because risk is often a function of versatility
and flexibility, which the business needs to respond to changing business trends and unexpected events like pandemics.
Establishing a Solid Foundation for a Vulnerability Management Program
Getting started with vulnerability management can be daunting for a new InfoSec professional starting at a new organization or establishing program at an existing company, but if you break down the major tasks into manageable pieces, you should be well-positioned
for success at the end of your first three months. It’s important to:
Find the assets and owners. Establish solid relationships with the asset owners – you need them to get anything substantial done.
Remember the goal. It isn’t to squash all the bugs and patch all the vulnerabilities (that’s impossible). It’s to squash and patch the ones that matter.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.