
Why Take a Pragmatic Approach to PAM?
By specifying control objectives, defining exception processes and prioritizing based on risk, the security team responsible for privileged access management (PAM) can enforce a set of smart PAM controls that please both IT and audit.
This piece explains how to create a pragmatic, audit-friendly approach to PAM, where controls can be ramped up or relaxed based on the overall risk to the organization.
PAM Control Objectives
Bring clarity to the PAM security capability by specifying the control objectives, independent from the implementation or technology. For example, common control objectives include, but are not limited to
Management of privileged accounts. The organization assigns privileged user accounts to individuals who require privileged access to perform assigned tasks and job-related duties. These privileged user accounts are unique to the individual, are not shared
accounts and are used only when necessary, to perform privileged activities.
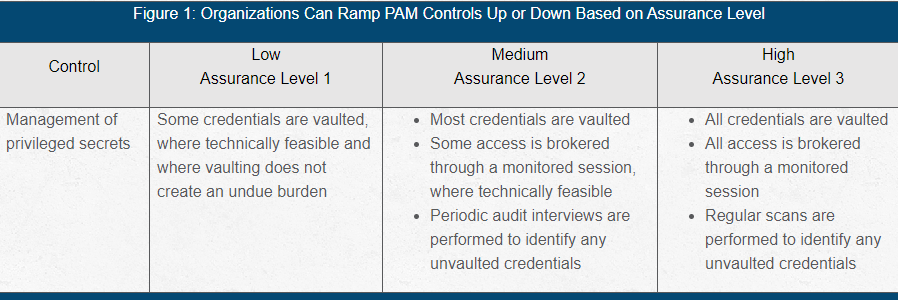
Management of privileged secrets. The organization protects privileged user accounts by vaulting their credentials. Passwords, shared secrets, private encryption keys and other credentials for privileged accounts are actively managed. Access is brokered
for people to perform assigned tasks and job-related duties.
Management of privileged access rights. The organization tightly controls the allocation and use of privileged access rights and restricts the use in accordance with the organization’s standards on least privilege and segregation of duties.
Privileged commands. The organization authorizes, monitors and audits the execution of privileged commands. Privileged users may only execute these commands while performing assigned tasks and job-related duties.
Use of privileged utility programs. The organization tightly controls and restricts the use of any utility program capable of overriding application controls and system controls.
Privileged access to sensitive data. The organization implements administrative and technical measures to restrict access to regulated data, including personally identifiable information (PII), payment cardholder data, etc.
Privileged access to sensitive systems. The organization implements administrative and technical measures to restrict access to system components processing, transmitting or storing of regulated data.
Privileged access. The organization authorizes, monitors and audits the access to security-relevant information. Privileged users may only access this information while performing assigned tasks and job-related duties.
Access enforcement. The organization tightly controls and restricts access into logical access controls (identification, authentication, authorization and accountability) such as Active Directory (AD).
Prohibit installation without privileged status. The organization configures systems to prohibit installation of software without explicitly using an authorized privileged account.
Appropriate knowledge and skillset. The organization hires or promotes people with the skillset and requisite experience to perform assigned privileged tasks and job-related duties. Individuals with privileged access receive appropriate operational training
and security training before accessing information systems.
Privileged account logging and monitoring. The organization maintains a process for linking administrative privileged accounts (e.g., domain admin or root) to the individual. Authenticating with privileged accounts is logged, monitored and reviewed.
Privileged functions logging and monitoring. Executing privileged functions and privileged utility programs is logged, monitored and reviewed.
Develop a Privileged Account Prioritization Matrix
Next, implement the control objectives above where technically feasible and when implementation does not put an undue burden on the organization in operating and maintaining the information system.
To appropriately prioritize the level to which the control is performed, consider:
- The number of systems the privileged account may access.
- The level of privileged access to which the privileged account is authorized.
- The operational risk of the systems and data in scope.
- The regulatory requirements and obligations of the systems and data in scope.
For example, a domain administrator with full access to business-critical applications and a Payment Card Industry Data Security Standard (PCI DSS) environment is a high-priority privileged account. Conversely, a low-priority privileged account would
be a database administrator with access to the tables of the development environment for one application.
To make management of privileged access easier, organizations should maintain a privileged account prioritization matrix and an information system criticality matrix. These are vital in ensuring controls are strictly applied for high-risk accounts and
high-risk systems, while allowing greater flexibility in interpreting controls in lower risk areas. Using these matrices, access can be given low, medium or high assurance levels. Then, you can interpret the control objective according to the appropriate
assurance level (see Figure 1).
Figure 1: Organizations Can Ramp PAM Controls Up or Down Based on Assurance Level
Exception Handling Process
When employing more relaxed controls in lower risk areas, it’s important to follow a fully documented exception handling process. Common exceptions include, but are not limited to:
- The operational need for shared accounts, e.g., root accounts.
- Privileged access that does not enforce segregation of duties, e.g., DevOps teams.
- Privileged functions, commands or utilities used by non-privileged accounts.
- Installation of software by non-privileged accounts, e.g., end-user endpoint management.
- Logging and monitoring gaps, e.g., legacy systems that can ship logs to the SIEM.
The decisions made under the process must be approved, documented, tracked and periodically re-assessed (at least annually). Ideally, these exceptions will have compensating controls, and if misused, will have a low impact on the overall organization.
PAM Implementation Tips
The best PAM security capabilities are fully documented with clear objectives and defined assurance levels. To ensure your PAM implementation is successful:
- Clarify the controls. Be sure to clearly communicate the objective, independent of implementation, technology or specific PAM tools.
- Rank privileged access. Use a privileged account prioritization matrix and an information system criticality matrix to ensure the control needs are clear.
- Manage exceptions. Use a repeatable exception handling process geared toward specific control objectives that are risk-ranked based on privileged access.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.