
What to Look for in a SOAR Solution
A truly effective security orchestration, automation, and response (SOAR) platform should incorporate the following critical priorities:
- A comprehensive function set in a single platform.
- An API-first architecture with simple integration built for extensibility and scalability.
- A user experience that ensures both end users and administrators are set up for maximum productivity.
- This piece explains the key features to look for in a SOAR platform and the top use cases to consider.
SOAR Solution Integrations
SOAR platforms offer many advantages, and among the most significant is the technology and tools integration to automate and streamline processes. A SOAR playbook can be integrated into products across various security technologies, such as cloud security, forensics, malware analysis, vulnerability and risk management, data enrichment, threat intelligence, incident response, and endpoint security, among others. The integration of these technologies into a SOAR solution can be seamless.
However, a lot depends on the SOAR tool you use and the SIEM you tie into. Not all platforms are created equal. For example, you may see distinct advantages having these solutions in one platform, or perhaps avoid tying into one single SOAR solution from your SIEM to prevent vendor lock-in.
Key SOAR Solution Features
When investigating options for a SOAR solution, consider the following:
Ease of integration: The number of security solutions within the IT security stack, whether they be in-house, outsourced, or commercial, is expanding exponentially. Every SOAR solution should be flexible enough to support a multitude of security products. It is crucially important that your SOAR solution of choice be flexible enough to allow security operations to easily create bidirectional integrations with security products not supported by default. The methods used to support these types of integrations could vary but might include scripting languages such as Perl or Python, APIs or proprietary methods. Regardless of the chosen method, it should be easy to implement, and the user should not be overwhelmed by the difficulty of use.
Ease of data ingestion: Bidirectional integrations are important in providing full automation and orchestration, but in some cases, an organization might not require full bidirectional functionality. For some security products, it may only be vital to support the ingestion of data from the security product to the SOAR platform. These unidirectional integrations are usually much easier to create. A SOAR platform should support common methods of data ingestion, database connections, APIs, email, and online forms, as well as common data standards, such as Common Event Format (CEF), OpenIOC and STIX/TAXII.
RESTful API support: When it comes to APIs, leveraging RESTful integrations is key. Standards-based APIs make it simple to link applications, so they can easily exchange data and procedure calls. Most SOAR platforms are compatible with multiple standards-based APIs, and in most cases. For example, with an API and corresponding standards-based web service, the SOAR solution can be configured to insert security alert ticket data into Jira without the need for proprietary application integration tools or custom coding.
SOAR Use Cases
SOAR use cases that provide value are automated incident response, threat intelligence automation, automated patching and remediation, employee provisioning and de-provisioning, and vulnerability management.
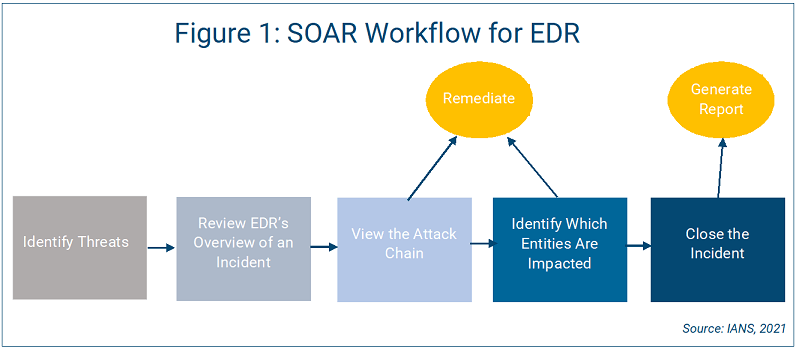
It’s important to define and continuously build workflows and playbooks for each use case. Figure 1 shows a workflow for endpoint detection and response (EDR), starting with threat identification and leading to remediation. Start simple, and then work on building out more complex use cases.
SOAR Solution Goals
Automate repeatable tasks. By automating the ongoing tasks associated with threat hunting and phishing in particular, your team will have more time to do what they do best: finding and thwarting the bad guys. Bring team members into this process strategically for maximum efficiency and remember that log/SIEM integration is key.
Notify and respond faster. Consider kicking off designated response workflows based on the type of threat you discovered. That will help ensure the proper stakeholders are notified as quickly as possible, and that everyone is working from the same set
of data for a complete end-to-end investigation. Sometimes, escalation can take valuable time and resources away from the issue at hand, especially when executives are involved.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.