
IAM Best Practices & Metrics to Monitor: Azure AD Security Features
Organizations can leverage Microsoft Azure for tooling in an identity and access management (IAM) program, but it requires clear objectives and goals for each capability within the program. This piece covers these and provides IAM best practices and metrics for measuring success or surfacing potential problem areas.
Microsoft and Identity Management
Microsoft has evolved and enhanced its approach to identity with the move to cloud services. In past years, organizations would deploy a suite of separate tools for identity governance, access management and privileged identity management. For some organizations and use cases, these can now all be covered with Microsoft’s Azure AD security features.
For example, Azure AD functionality can help automate and simplify cloud IAM for the following areas:
- Identity lifecycle
- Access control
- Application lifecycle
- Access reviews
- Multi Factor authentication (MFA)
- Conditional access
- Privileged identity management
Goals and metrics for each of these are addressed below.
READ: Centralized IAM Best Practices
Identity Lifecycle
The human resource management system (HRMS) should be the central source of truth for the workforce. When employees are hired and HR adds them into the HRMS, they should also be created automatically in Azure AD. When changes occur, such as the employee’s name or manager, HR should update the employee information in the HRMS, and these changes should be automatically synchronized in Azure AD. When the individual is no longer employed by the organization, this too should be automatically reflected in both the HRMS and Azure AD.
At the time of this writing, Azure AD natively supports Workday and SAP SuccessFactors. It is important to note if you use another HRMS, additional steps may be involved.
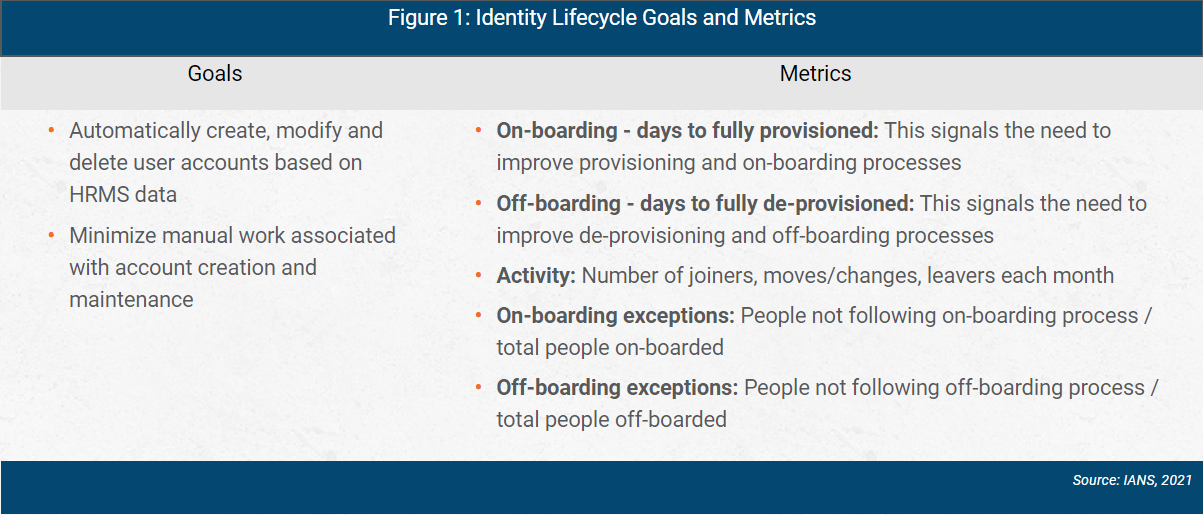
Identity lifecycle goals and metrics are shown in Figure 1.
Access Control
People in the workforce should have access to the resources they need to complete their job duties. This access should be automatically provisioned based on their job role or through aspects of their work, i.e., through a combination of role-based access control (RBAC) and attribute-based access control (ABAC). Manual provisioning of applications and access should be minimized.
AD has long supported RBAC through group membership. Azure AD introduces dynamic groups, where membership is based on user attributes. Most of the access should be granted through the information synchronized with the HRMS, reflected in Azure AD group memberships.
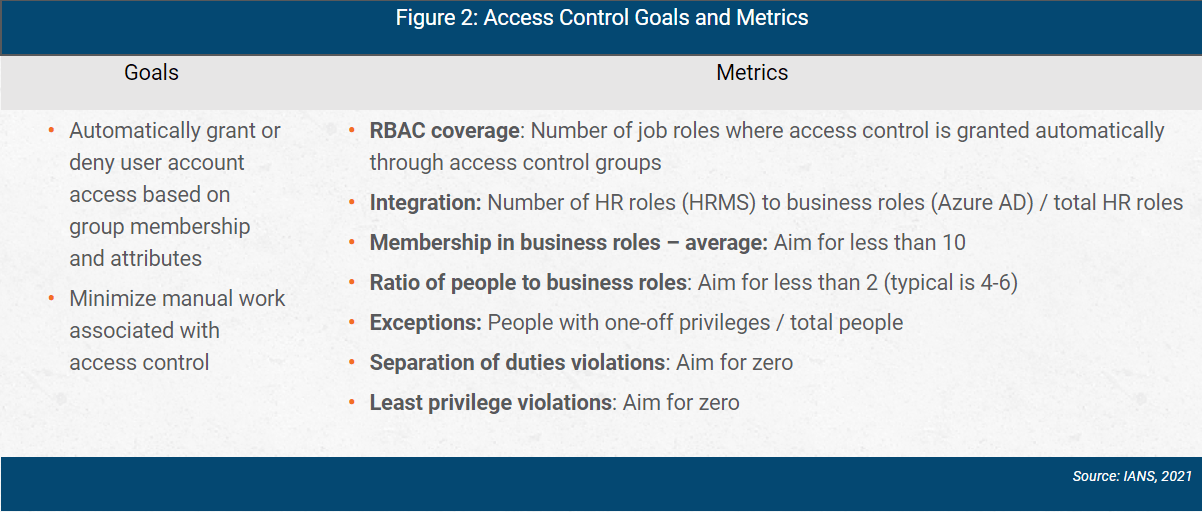
Access control goals and metrics are shown in Figure 2.
Application Lifecycle
User accounts and access controls (groups, roles, attributes, claims) exist in both the identity provider and in the application. This can create risk if the application owner over-provisions a user or delays in removing accounts when the organization revokes a person’s access and removes their account in AD and the HRMS. Ideally, the application tightly integrates with the identity provider, and creation, modification and deletion of accounts is synchronized.
Azure AD supports such application integrations through systems for cross-domain identity management (SCIM). When the application doesn’t support SCIM, Azure AD can achieve the objective of identity synchronization using federation protocols such
as security assertion markup language (SAML) and Open ID Connect (OIDC).
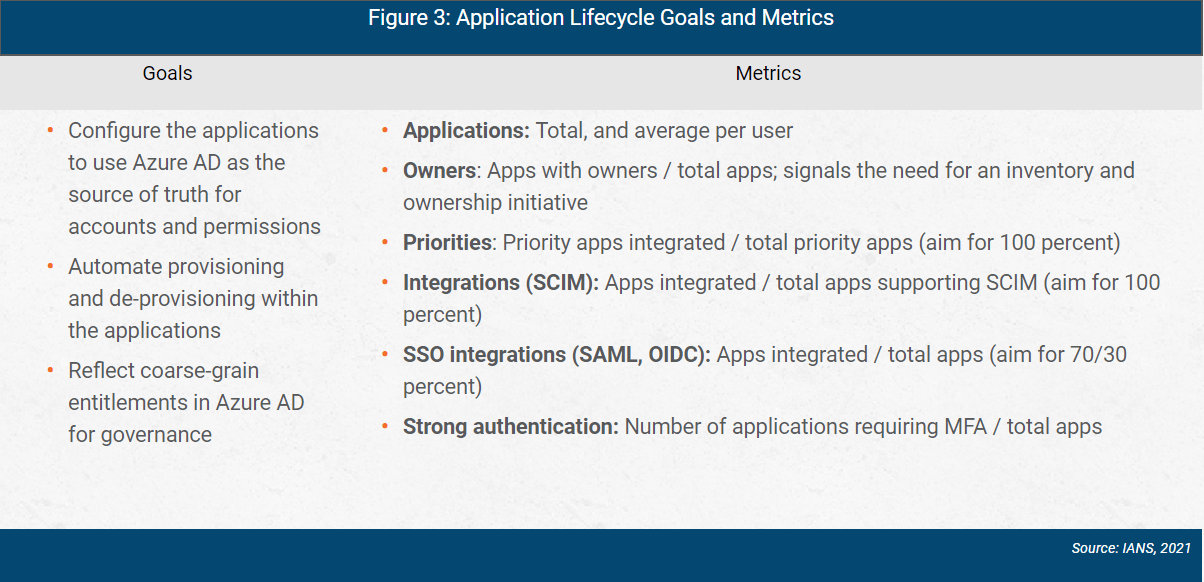
Application lifecycle goals and metrics are shown in Figure 3.
Access Reviews
Appropriate access shifts over time due to edge cases where automation isn’t effective, or manual efforts outside of normal provisioning. At best, this results in out-of-role access. At worst, it can result in toxic combinations and separation of duties (SoD) violations. Periodic access reviews help prevent these risks from occurring. Access reviews also can uncover stale accounts, orphaned accounts and over-provisioned access. These point to gaps in process and identify opportunities for improving account automation and access control (i.e., RBAC and ABAC).
Azure AD provides access reviews and certification programs as a component of identity governance. These reviews are tied to specific groups and performed by group owners or designated reviewers. Azure AD provides recommendations during the review process, for example, removing individuals who have not used their accounts in months.
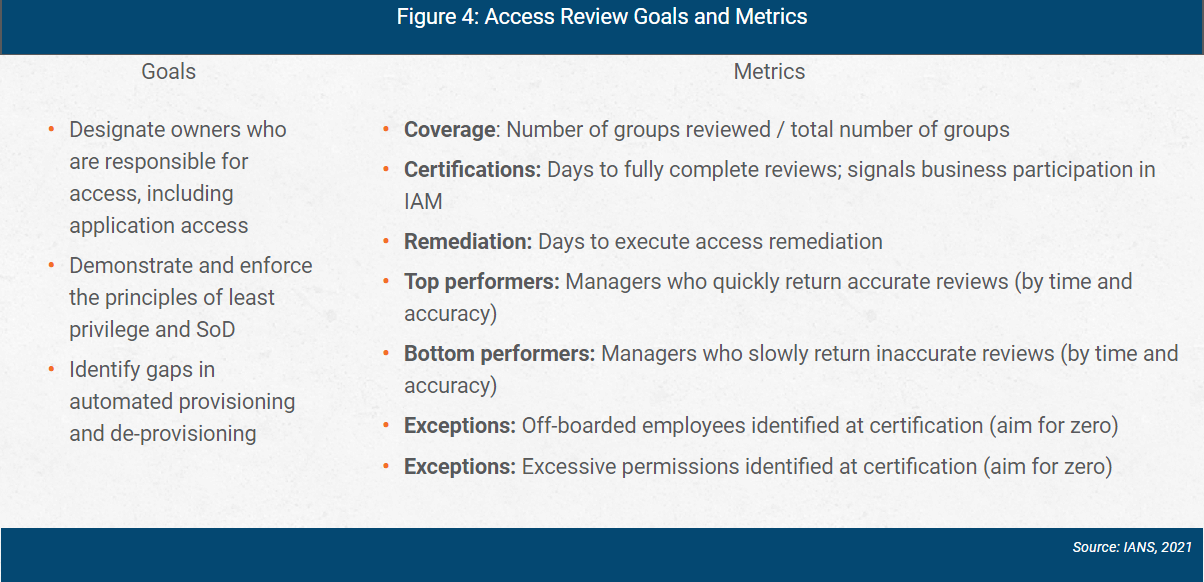
Access review goals and metrics are shown in Figure 4.
Multi Factor Authentication
MFA adds additional factors of authentication to the primary factor which is, typically, a text password. Azure provides MFA through a combination of factors, providing a strong authentication for applications and resources.
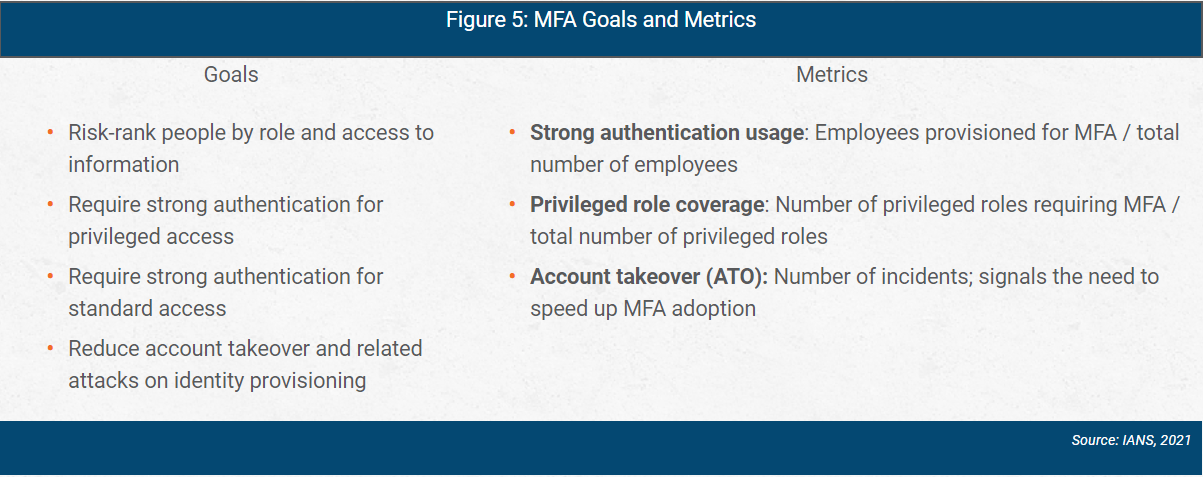
MFA goals and metrics are shown in Figure 5.
Conditional Access
We trust identities to use the privileges we’ve assigned them. This can be as simple as an identity knowing the password for its user account (primary authentication factor). While the principle of least privilege has been consistently improved with access controls, the principle of least trust around identities connecting to resources has only recently begun to be developed. In modern systems, we consider the context and conditions of authentication before allowing user accounts to access applications and resources.
Azure AD collects signals of trust on authentication and enforces decisions based on these signals. Examples of signals include location, device state or risky behaviors. Decisions include block, allow or require stronger authentication. Collectively, this is the conditional access feature in Azure AD.
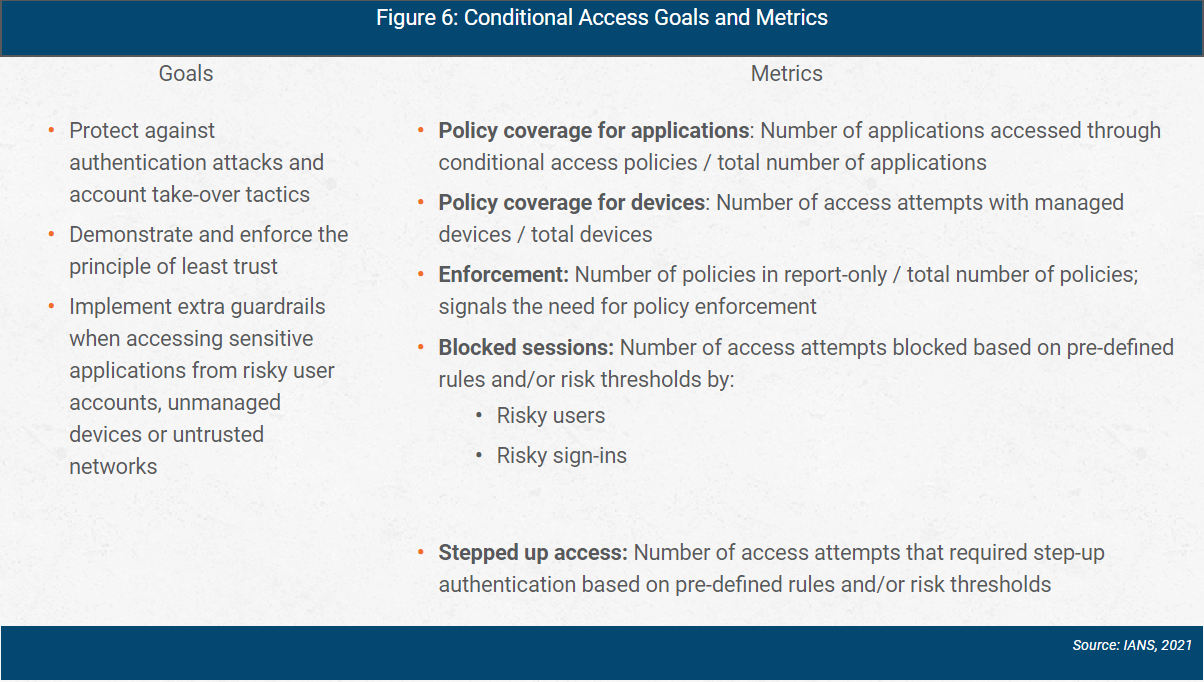
Conditional access goals and metrics are shown in Figure 6.
Privileged Identity Management
Privileged identity management (PIM) and privileged access management (PAM) are capabilities for enforcing least privilege and SoD for accounts with administrative-level access. PIM/PAM build on IAM concepts previously discussed; they require role-based access and access reviews, enforce strong authentication, and validate trust before privileged access. PIM also includes the concept of just-in-time access and time-bound access to limit the time an account has elevated access to the environment.
Azure AD includes PIM functionality to manage and monitor privileged access to Azure and Office 365 resources.
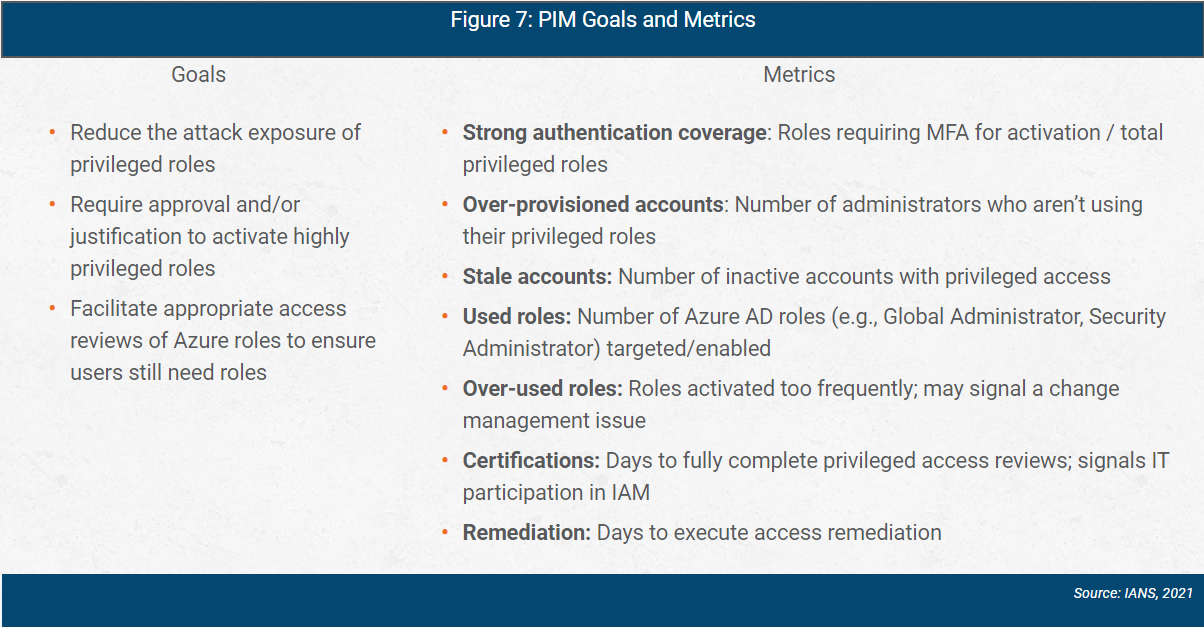
PIM goals and metrics are shown in Figure 7.
Identity and Access Management with Azure AD
Azure offers several features to make out-of-box IAM in the cloud possible. To be successful consider the following IAM best practices:
- Set clear goals and measure progress: Clear metrics will ensure you get the most out of Azure AD and remain focused on security fundamentals while deploying Microsoft’s features.
- Take a methodical approach and focus on feature value: Azure offers several features, and it is possible to deploy settings that don’t advance the identity program or reduce the risk. Be mindful in deploying and enabling security controls.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.