
How to Transition from NIST SP 800-53 Rev. 4 to Rev. 5
NIST SP 800-53 Rev. 5 represents a significant restructuring vs. Rev. 4, including a new focus on privacy. This detailed how-to provides a structured
plan to help organizations successfully transition from NIST SP 800-53 Rev. 4 to Rev. 5 controls within their security and privacy management programs.
NIST SP 800-53 Rev 4 vs. Rev. 5 Comparison
SP 800-53 Rev. 5 is not simply an update to Rev. 4; it is a major restructuring of this important information security (and now privacy) controls document. To support a successful transition from Rev. 4 to Rev. 5, it is helpful to understand the primary,
substantial changes that were made. These include:
- 269 additional/new controls, including 65 new base controls and 204 enhancements. Fully 42 of the new controls are specific solely to privacy, and 28 additional controls are exclusively specific to personal data, personally identifiable
information (PII) and similar terms.
- Consolidation of controls. Privacy controls were included extensively throughout the updated catalog. In addition to the 70 new controls exclusively focused on privacy and/or on personal data, privacy was also incorporated throughout
the rest of the catalog controls and enhancements, where applicable. This establishes a consolidated control catalog for both information security and privacy.
- New supply chain risk management (SCRM) control family: SCRM was introduced as a new control family, and additional SCRM-related controls were also incorporated throughout the full catalog controls, where applicable.
- New program management (PM) control family: The PM controls are based on the latest threat intelligence and cyberattack data (e.g., controls to support cyber resiliency, secure system design, security and privacy governance, and accountability).
Controls are rewritten to be outcome-based. Those using Rev. 4 and earlier versions will quickly notice this change. Prior versions framed the control by responsibility, but the new version instead describes the outcome of the control.
Figure 1 provides an example using verbatim content language from control RA-1, “RISK ASSESSMENT POLICY AND PROCEDURES,” with the key changes in the Rev. 5 update in orange.
Figure 1: Comparing Control RA-1 in Rev. 4 and Rev. 5 | |
Rev. 4 | Rev. 5 |
Control The organization:
| Control a. Develop, document and disseminate to [Assignment: organization-defined personnel or roles]:
b. Designate an [Assignment: organization-defined official] to manage the development, documentation and dissemination of the risk assessment policy and procedures; and c. Review and update the current risk assessment:
|
Source: IANS, 2021 | |
In effect, this expanded the management activities, scope of applicability and frequency of risk assessments. Also, by dropping the entity that performs the controls, it removes the implication the risk assessment must be performed by the organization
itself; contracted entities can perform this control. Organizations moving from Rev. 4 to Rev. 5 will need to review their risk assessment policies and procedures, and update them to reflect these changes, if they have not already been doing these
activities.
Similar impacts also resulted in the other updated controls. And because of the change from organization-based controls to outcome-based controls, generally every existing Rev. 4 control was updated, withdrawn or incorporated into another control in the
Rev. 5 catalog.
Additional NIST SP 800-53 Rev. 5 Changes
In addition to the changes detailed above, Rev. 5 also:
- Improves descriptions of content relationships by providing clarifications of the relationship between requirements and controls, and of the relationship between security and privacy controls.
- Separates the controls selection processes from the actual controls themselves. This helps make clear that security and privacy controls are not just meant for use by the U.S. federal government, but by all types of organizations,
in any type of industry, and by a wider variety of information assurance professionals, such as systems engineers, software developers, enterprise architects, security architects, systems security and privacy engineers, physical safety and security,
and business owners, to name just a few examples.
- Removes the federal control baselines and tailoring guidance from the primary NIST SP 800-53 document and makes it a separate document, associated to the new NIST SP 800-53B, Control Baselines for Information Systems and Organizations.
This document contains three security baselines and one privacy baseline established for federal agencies to support their specific requirements under the Federal Information Security Modernization
Act (FISMA) and the Office of Management and Budget (OMB) Circular A-130. While they were created specifically for federal
agency compliance, they provide excellent models for other organizations to use when developing their own customized baselines to meet their organization’s and/or industry’s risk management needs and legal requirements.
In addition, organizations transitioning from Rev. 4 to Rev. 5 should find NIST’s analysis of the Rev. 4 to Rev. 5 updates beneficial.
Steps to Transition from NIST SP 800-53 Rev. 4 to Rev. 5
The following steps should help your organization transition from Rev. 4 to Rev. 5 efficiently and effectively.
Step 1: Understand the Control Families
SP 800-53 uses 20 different control families (see Figure 2).
Figure 2: NIST SP 800-53’s 20 Security and Privacy Control Families | |||
ID | FAMILY | ID | FAMILY |
AC | Access Control | PE | Physical and Environmental Protection |
AT | Awareness and Training | PL | Planning |
AU | Audit and Accountability | PM | Program Management |
CA | Assessment, Authorization, and Monitoring | PS | Personnel Security |
CM | Configuration Management | PT | PII Processing and Transparency |
CP | Contingency Planning | RA | Risk Assessment |
IA | Identification and Authentication | SA | System and Services Acquisition |
IR | Incident Response | SC | System and Communications Protection |
MA | Maintenance | SI | System and Information Integrity |
MP | Media Protection | SR | Supply Chain Risk Management |
Source: IANS and NIST, 2021 | |||
Step 2: Establish a Transition Work Team
Assign specific review responsibilities for all 20 families to team members. Include team members who have worked in some way with meeting the Rev. 4 controls compliance, and who also have expertise in the families they will be reviewing. For example,
designating team members from the human resources (HR) area to review the personnel security controls will be beneficial, since they should have good insights about that topic. Similarly, key stakeholders from the privacy or compliance department
should be able to provide insights for all the new privacy- and personal data-specific controls.
Organizations should provide each member of the transition team with:
- A copy of Figure 3 in this document.
- A copy of SP 800-53 Rev. 4 and any documentation that shows the mapping to the organization’s security and privacy program, such
as corporate policies, procedures, etc.
- A copy of SP 800-53 Rev. 5
- The elements included in Figure 3 below describing how the associated controls were modified in Rev. 5 from Rev. 4.
Step 3: Get to Work
Each team member should:
- Identify the updated and new controls in Rev. 5 that are not applicable to the organization. Figure 3 should be helpful here. Have each team member identify and eliminate the controls within each family the organization does not use
and still does not need after any revision to the controls. Each team member should briefly document why they determined the control could be eliminated. This will allow you to narrow your scope of consideration to only those actions applicable
to your organization.
- Identify the controls changed from Rev. 4 to Rev. 5 that do not affect the organization’s practices. This will likely be the case for controls that had only minor changes, or that did not change scope or activities. Each team
member should briefly document why they determined the control does not require changes. This will provide traceability that demonstrates the control was reviewed, not overlooked.
- Identify the controls eliminated from Rev. 4 and not incorporated into any Rev. 5 control. Document these to then review, as a team, to determine whether they are still needed within your organization, based on the organization’s
risk environments, established practices, systems and applications, etc.
- Identify the controls materially changed from Rev. 4 to Rev. 5. The associated actions the organization takes for those controls will then need to be updated. For example, earlier we pointed out how the RA-1 control was changed in
such a way that the scope of applicability and frequency were changed. You will need to make sure the associated risk management and risk assessment procedures, processes and any associated tools are also changed.
- The controls left should be those that are new in Rev. 5. Have each team member provide a brief recommendation for actions necessary to comply with each control.
Once you’ve followed these steps, you should have the action plan necessary to ensure complete transition from Rev. 4 to Rev. 5.
Figure 3 provides an excerpt from the NIST spreadsheet listing all the new base controls and control enhancements. The excerpt shows only the new base controls and new enhancement controls sorted into those two topics.
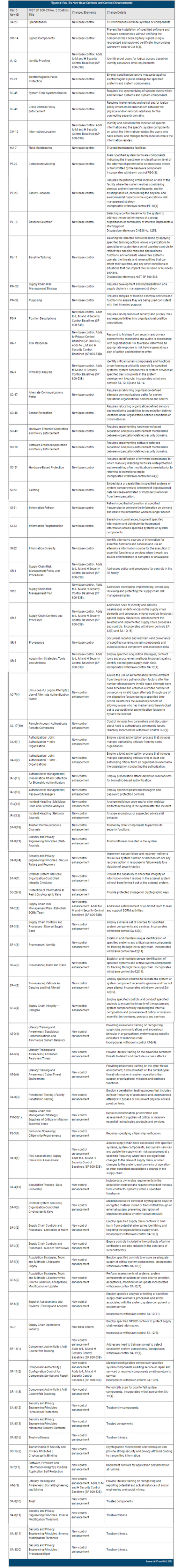
NIST SP 800-53 Rev. 4 to Rev. 5 Transition Tips
Moving from NIST SP 800-53 Rev. 4 to Rev. 5 requires attention to detail. To increase your chances of success:
- Review and understand the control families. Rev. 5 uses 20 control families, many of which require new focus on privacy and personal data.
- Use a team of experts: All team members should fully understand their assigned control family and be equipped with the right tools to judge how the changes in Rev. 5 impact the organization.
- Vet the changes and their impact in a systematic manner. Each change must be examined to determine its applicability as well as its effect on current processes and procedures.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.