
How to Develop a Cybersecurity Training Program
January 4, 2022
Is your organization impacted by the shortage of cybersecurity talent? Find best practices for developing a cybersecurity training program that can ramp up even non-security staffers in an efficient, comprehensive way.
IANS Faculty
As organizations continue to face a workforce shortage and struggle to hire and retain cybersecurity talent at all experience levels, many are taking non-traditional approaches, such as training non-cybersecurity employees to fill the gap. This piece shares best practices on how to develop a training program that can ramp up even non-cybersecurity staffers in an efficient, comprehensive way.
Organizations should attempt to be disciplined in how they approach training both traditional and non-traditional cybersecurity staff to manage cybersecurity risks and be resilient in the face of cyberattacks, such as training developers secure coding basics. A well-defined training program with key objectives can begin to address cybersecurity needs by quickly ramping up the skills and capabilities of a cybersecurity team.
Developing a Cybersecurity Training Program
Developing a cybersecurity training program project plan is one of the best ways to ensure you don’t veer off course. The project plan establishes the tasks, schedule and milestones, and should encompass the following six steps.
1. Do a Cybersecurity Training Needs Assessment
The training needs assessment should be specific to your organization. Because it is focused on cybersecurity, a good way to start is to create an org chart for the cybersecurity team and roles, and then define the tasks each role must perform. Once the tasks are defined, you can create a knowledge and skills matrix that can be decomposed into training topics.
We suggest creating job ladders for each role to address levels and to show a career path. This can help motivate employees to continue learning and improving, and it also establishes expected milestones to achieve when it comes to knowledge, skills, abilities and performance for promotion.
One of the more comprehensive resources for cybersecurity workforce roles and knowledge, skills and abilities (KSAs) is the NIST National Initiative for Cybersecurity Education (NICE) framework. The NICE framework consists of:
- Categories (7): A high-level grouping of common cybersecurity functions.
- Specialty Areas (33): Distinct areas of cybersecurity work.
- Work Roles (52): The most detailed groupings of cybersecurity work comprising specific KSAs required.
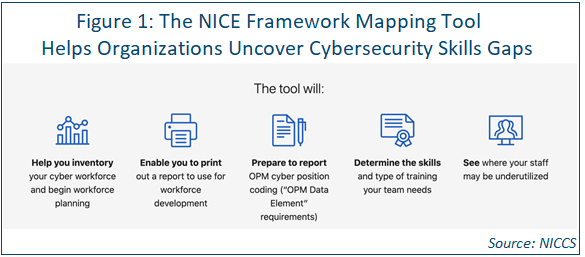
Taken directly from the Center for Internet Security (CIS) the NICE framework is an important high-level tool for organizations trying to improve how they identify, recruit, develop and retain cybersecurity talent by enabling them to better define their cybersecurity workforce and identify gaps in staffing. The National Initiative for Cybersecurity Careers and Studies (NICSS) also provides a NICE Framework Mapping Tool that eases the process (see Figure 1).
LEARN MORE: IANS' Online Training
2. Establish Cybersecurity Training Objectives
Training objectives are what workers should be able to do after the training is completed. When developing a cybersecurity training program for a workforce that may be brand new to the topic, it is important to address three key topics:
- General cybersecurity fundamentals: Dozens or even hundreds of organizations offer training on cybersecurity fundamentals, including ISACA, Udemy, Coursera, CompTIA and multiple community colleges and universities. There is even free training available on YouTube. This is intended to baseline everyone on the basics of cybersecurity concepts.
- Organization-specific business objectives and cybersecurity needs: When it comes to your organization, training objectives should consider including understanding business objectives, goals and how success is measured for the organization. Why is this important? A cybersecurity team could be doing a bunch of activities that are good for security, but they may not be targeted at what is MOST important to the organization. With limited resources, it is critical for the cybersecurity team to understand where they should spend their time and money. For example, if the organization has planned an acquisition for the coming year, the cybersecurity team should focus on the merger and acquisition (M&A) security practices that will be necessary (e.g., third-party security practices).
- Individualized hands-on experience and continuous training topics: Training objectives should also outline what hands-on experience will be used to put the learning into practice. The plan should also address continuous learning topics for the next 1-3 years (use your budgeting cycle to determine the length of time).
When writing the objectives, focus on addressing KSAs and ensure they are specific, measurable, achievable, relevant and time-bound (aka SMART).
3. Develop Cybersecurity Training Materials
Some common guidance (edited from Vector Solutions) on designing, developing or identifying/buying training materials includes:
- Focus solely on employee needs, and not on what’s easy, fast or cheap.
- Use only materials that relate directly to your learning objectives. Focused, lean training without filler material will ensure your main objectives are clear and concise. Extra text, graphics and videos can lead to cognitive overload and dilute learning.
- Include as much hands-on practice or simulation as possible. People learn by doing.
- Let employees drive it. Whenever possible, put the employees in control of the learning process to foster buy-in and appeal to all types of learners. Some people love videos, while others have better retention through reading. Some people learn better in short snippets, while others will motor through training in one sitting.
- Allow opportunities for learning in groups to foster team collaboration.
- Ensure there’s plenty of opportunity for feedback during training. Good training is iterative and constantly improves and evolves.
- Break your training materials up into small chunks. That way, it is easier to take in and understand.
- Order it in a logical manner. One step should build on top of another, or chronologically, etc.
- Try to use a “blended learning” approach that includes training in several different formats (computer-based, instructor-led, etc.).
- Integrate gamification where possible.
The material should always be tailored to the roles outlined in the org chart. This ensures you cater training specifically to individuals and the needs of the organization for that individual.
4. Implement the Cybersecurity Training
Engaging the employees early by sharing the training program plan is an important step for buy-in and success. Explain the objectives, the way training will be provided (online, in person, self-paced, synchronous, etc.), when training will be provided, expectations for completion and how to provide feedback.
Consider how your organization provides other training and the learning management system (LMS) used. Will the cybersecurity training use the same platform? Will team members be expected to travel to training? Will they be able to pace the learning themselves?
5. Evaluate the Cybersecurity Training
Evaluation has several important aspects to consider, including:
- Feedback: It’s important to understand and gauge employees’ reaction to the initial training to make future training something everyone wants to complete.
- Actual learning: Actual learning can be measured via assessments, tests, simulations or hands-on exercises. Remember, few adults want to be “tested,” so how this is messaged is critical. Is the assessment a pass/fail? What performance level is expected? What happens if the expected level is not achieved? This needs to be explained BEFORE the assessment is provided.
- Organization results: Finally, and perhaps most importantly, what changes/benefits do you expect the organization to have after the training is complete? Are your cybersecurity capabilities improving? Are you seeing fewer incidents or perhaps more incidents discovered but addressed early? Knowing what you want to improve within the organization is important to knowing if the training is taking the team and organization in the right direction.
6. Focus on Lessons Learned
After the training program completes a cycle, the organization should identify what worked, what didn’t and what is needed for the next cycle. At this phase, training may either go into regular execution or a brand new training program plan may need to be developed.
A common mistake in training non-cybersecurity staff is trying to cover too much at once. Start with an overview of cybersecurity fundamentals, but then use the org chart to allow staff to focus with some depth on the specifics of their role. For example, a cybersecurity incident response engineer will not need to have deep training in cryptography.
Cybersecurity Training Pitfalls to Avoid
Taking the time to develop a cybersecurity training project plan ensures the training program is aligned with business objectives and needs. Common pitfalls to consider when making the plan include:
- Not being pragmatic. How much training is realistic? What media is best for your team?
- Cognitive overload. Training employees over time and giving them the opportunity to apply the concepts to their daily jobs is highly recommended.
- Poor user experience. Is the LMS clumsy? Is the training monotonous and boring? Would the training be better suited in small teams rather than alone?
- Lack of alignment with business objectives. I cannot stress this one enough!
- Not gathering feedback. You may not get everything right the first time, but the employees can help correct direction and improve things for next time.
Cybersecurity Training Program Best Practices
Training up a team, especially staffers with very little to no cybersecurity experience, can be difficult. To be successful, organizations should consider:
- Plan the program carefully and start with a cybersecurity training program plan.
- Ensure the training is comprehensive and covers:
- General cybersecurity fundamentals.
- Organization-specific business objectives and cybersecurity needs.
- Individual hands-on experience and continuous training topics.
- Evaluate the training. Measure your cybersecurity capabilities and determine if these improve after training is provided.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.
We use cookies to deliver you the best experience on our website. By continuing to use our website, you consent to our cookie usage and revised Privacy Policy.