
How to Create a Temporary SOC 2 Alternative
For security teams that have not yet completed a SOC 2 due to time and budget constraints, it is possible to come up with a workable alternative using internal resources.
This piece provides guidance for the process of building an interim compensating controls document (CCD) that can be used with customers until a full SOC 2 process is complete.
Create a CCD as a SOC 2 Alternative
Service Organizational Controls 2 (SOC 2) Type 2 is the lowest barrier for entry to build customer trust, along with ISO 27001. Without it, you will likely spend an inordinate amount of time providing the same information over and over to prospects and clients. Creating a formal compensating controls document (CCD) built along similar lines to a SOC 2 (attesting to similar controls and processes) can help but should only be used as an interim step until buy-in/budget for a full SOC 2 can be attained.
If you don’t have an attested program with a credible third-party certification, it makes building trust difficult and you will likely have to provide the same information over and over again to each prospect and customer. However, demonstrating your compensating controls in an organized document will help tremendously.
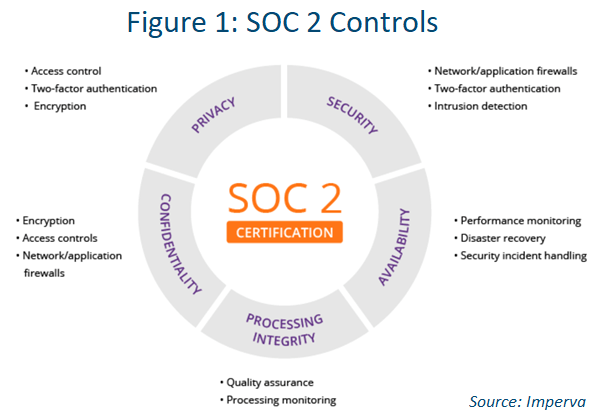
Your CCD should contain a list of findings and a checklist of compliance requirements. The key areas of focus should be:
- Availability
- Confidentiality
- Process integrity
- Security
- Privacy
An official SOC 2 allows plenty of room for interpretation, because every organization has its own requirements based on the way it operates. With that in mind, the CCD should provide the following (just like a SOC 2):
- An opinion letter, which basically lays out the company stance on the attestations within the CCD.
- Management assertion, which underscores C-level support.
- A detailed description of the system or service.
- Details of the selected trust services categories (see the list here).
- Tests of controls, including the steps and procedures for testing (for example, quality assurance reviews for access controls).
- Any optional additional information.
These kinds of control statements help build trust and confidence in your capability to pull off a SOC 2 (see Figure 1) in the future.
READ: Continuous Compliance Best Practices
CCD Example
You may already have much of this information in your current resources, for example, a data processing agreement (DPA) associated with the EU’s General Data Protection Regulation (GDPR). The following provides an example of what will be needed (items in orange can be customized to your organization):
SAMPLE COMPENSATING CONTROLS DOCUMENT (CCD)
ACCESS CONTROLS. Access to data must be limited to only those [INSERT NAME OF COMPANY] personnel who have been authorized by [INSERT NAME OF COMPANY] and have a clear operational need for such access. [INSERT NAME OF COMPANY] will maintain access controls for all environments holding data used in connection with [INSERT NAME OF COMPANY], including without limitation, use of two-factor authentication such as access-controlled facilities in conjunction with user ID and password, or user ID and one-time-use password.
DATA PROTECTION. [INSERT NAME OF COMPANY] will protect electronic data used in connection with [INSERT NAME OF COMPANY] Service. Content at rest will be encrypted with a solution that uses 256-bit Advanced Encryption Standard (AES) or better industry-standard algorithms. Data in transit shall be protected using TLS 1.2 encryption or stronger.
DATA BREACH. means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure or access to personal data transmitted, stored or otherwise processed.
In the event of an incident, [INSERT NAME OF COMPANY] shall make available key personnel with sufficient knowledge to resolve any data privacy or security issues involving content or data exporter Information, and in particular, work with the data exporter to determine the scope of the incident, investigate the incident, and prepare a written summary of the incident and corrective action taken; however, such efforts shall not alter or change responsibility between [INSERT NAME OF COMPANY] and the data exporter for providing such notifications under applicable laws.
BUSINESS CONTINUITY/DISASTER RECOVERY REQUIREMENTS
MAINTENANCE OF PLAN. [INSERT NAME OF COMPANY] shall maintain and comply with a reasonable disaster recovery, crisis management and/or business continuity plan (the “Plan”) which is capable of ensuring [INSERT NAME OF COMPANY] shall be able to continue to provide the [INSERT NAME OF COMPANY] Service in accordance with this agreement in the event of a disaster or other significant event (including a force majeure event) that might otherwise impact [INSERT NAME OF COMPANY]'s operations.
TESTING THE PLAN. [INSERT NAME OF COMPANY] shall test the Plan with respect to the [INSERT NAME OF COMPANY] Service no less than once each year. On request, [INSERT NAME OF COMPANY] will provide the data exporter with a summary of the results of such test. [INSERT NAME OF COMPANY] will notify data exporter of any material failures in its disaster recovery or business continuity capabilities that [INSERT NAME OF COMPANY] believes would be reasonably likely to impact [INSERT NAME OF COMPANY]'s performance of the Services.
READ: Key Components of an Effective Business Continuity Plan
SOC 2 Recommendations
Consider the following steps to help solve this problem in the short and long term:
- Get a roadmap together for a SOC 2 Type 2. Use a reputable third-party auditor. This helps build trust and show you have a long-term strategy/plan.
- Build a CCD. This is a solid short-term fix that will be backed up by your long-term roadmap to SOC 2. It should look similar to a SOC 2 report and should leverage:
- Your current access control, encryption and business continuity/disaster recovery information.
- Your privacy statement or DPA.
- Begin working on a budget and executive buy-in for a SOC 2. Build the use case on revenue impact, meaning how much revenue is being lost by NOT having a SOC 2 in place (e.g., win/loss of deals). A good place to gather this data is in a customer relationship management (CRM) tool like Salesforce. You could put a field into opportunities and renewals that require a SOC 2, and then run a report on the estimated value of the deal and win/loss records.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.