
Creating a Threat Model in 4 Efficient Steps
In this piece we provide a checklist for how to use third-party research assets to analyze the threat landscape and create an industry-specific list of threats impacting your business. As part of this checklist, you’ll also find a series of helpful reports to use in your analysis.
What is a Threat Model?
Your organization’s threat model is a fact-based high-to-low ranked list of the top 3-6 cybersecurity circumstances that could bring harm to the business.
High threat is a credible combination of likelihood of the event plus short-and long-term damage to the company. It is ranked but not deeply quantitative. It should serve as a meaningful aid to risk conversations with top leadership and your board. A
simple example of a home threat model is shown in Figure 1. Your company’s cybersecurity threat model might include direct network penetration and data exfiltration, ransomware, denial of service on customer sites, malware disrupting manufacturing,
insiders leaking intellectual property (design or sales information), etc.
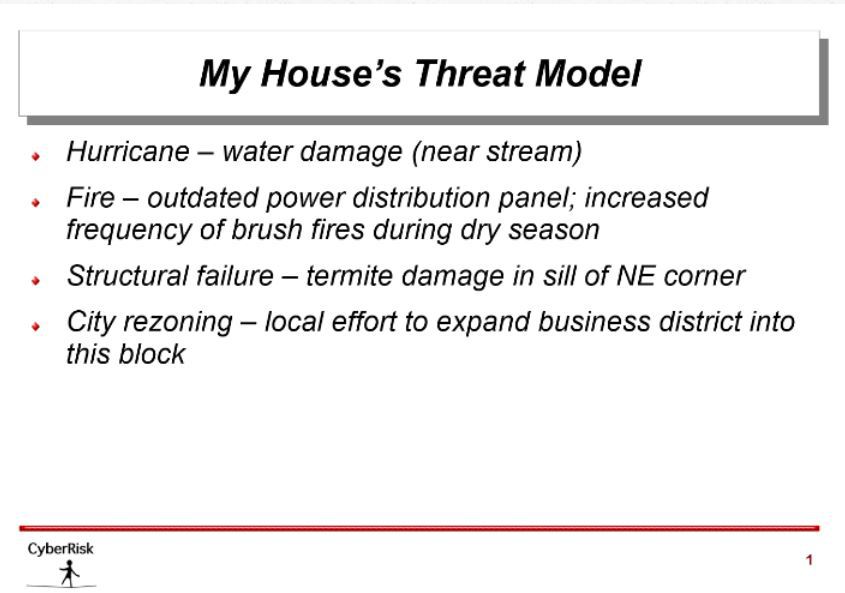
How to use the Threat Model/Industry Research Workflow
The checklist below provides tools and resources to help you create an initial industry threat list. This list is the starting point for creating a custom threat model for your business. Your goal is to find credible sources that provide insight into the current threat landscape as it impacts your business.
READ: Creating an Effective Cyber Threat Intelligence Framework
Threat Model/Industry Research Workflow
This checklist shows how to use available industry resources to build a threat list that can feed a custom threat model for your business.
1. Choose a Resource
- Primary threat intelligence sources:
- Similar reports from other vendors
- Sector and company specific reports from consulting firms, network security practices or threat intelligence providers
- International and governmental risk/threat reports:
READ: Key Phases of an Effective Global Threat Response Playbook
2. Consider the Resources Release Frequency
- For example, the Verizon DBIR is released annually each spring
3. Determine its Pros and Cons
- Verizon DBIR Pros:
- Easy to read (for a security report)
- Summarizes broad trends with data-based summaries that map to industry sectors
- Patterns are clearly described and continually improved
- Graphics provide helpful explanations
- Verizon DBIR Cons:
- Graphics may not appropriate for executive/board-level audiences
- Graphics may not appropriate for executive/board-level audiences
4. Perform a step-by-step analysis
- Read cover to cover (or at least skim) to understand the basic layout
- Start at the 50,000-ft. level and look for worldwide trends
- Note the careful definitions and align them with your reading of other reports
- Ensure any data or graphics you use employ the same definitions, and adjust each element of your presentation accordingly
- Move to the 10,000-ft. level and look for industry trends
- Review industry descriptions to ensure your industry is properly characterized
- Consider using data from your industry and that of one of your customers, e.g., a medical device company might use data from both manufacturing and healthcare to build a comprehensive view of applicable threats
- Ensure the data/graphics you choose to use as takeaway points are clear and do not require more than a sentence of explanation
- Skim the last two or three reports for any data that helps understand trends in your industry and business
- Note those trends, relate community experience and extrapolate forward
The choice of threat reports should be customized for your needs. There is a seemingly infinite supply of reports. Don’t be intimidated – choose a few meaningful ones to start and let your library evolve. Large security companies issue annual reports together with breach and threat-specific reports. Explore the reports that your major security vendors issue. These can have special credence to your organization. You also might be able to reach beyond the reports into the vendor company’s threat team to get more specific and meaningful information.
Your threat model will change. Annual revisiting is essential but ongoing changes in the threat landscape, your business exposure and recent high-profile exploits all warrant reconsideration and possible revision.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.