
Microsegmentation Best Practices to Mitigate Malware
Implementing proper microsegmentation and measuring its effectiveness against malware and other attacks is never straightforward. The technologies, products and enforcement methods vary wildly, making product selection and configuration challenging.
When the idealistic model of 1-to-1 access policies is not possible, enclave-based deployments based on asset value and risk are most appropriate. Solutions for this in data center vs. traditional LAN networking vary greatly, and products for one will not suffice for the other. However, any measurement of effectiveness of segmentation should be a metric based on the risk model.
This piece details the different types of microsegmentation along with their challenges and provides recommendations to implement microsegmentation successfully.
Network Segmentation Definitions
Proper network segmentation (regardless of the specific implementation) is still the leading mitigation against malware and attacks that rely on lateral movement within the environment. Organizations of all sizes and industry verticals face this same challenge of proper network segmentation, and many are beginning incremental implementation of zero trust architectures. This move was accelerated by the COVID-19 pandemic, the work-from-anywhere (WFA) model and the prevalence of organizations moving services to the cloud.
It’s helpful to understand that “east-west” and “north-south,” as well as the term “microsegmentation,” are often used differently by vendors in traditioned LAN networking versus the data center. For the purposes of this document, north-south traffic is defined as traffic coming in from or out of the network edge up through the core to the data center and possibly the internet (see Figure 1). East-west describes any peer-based data paths, including those among edge devices and/or within peer data center workloads, services or applications.
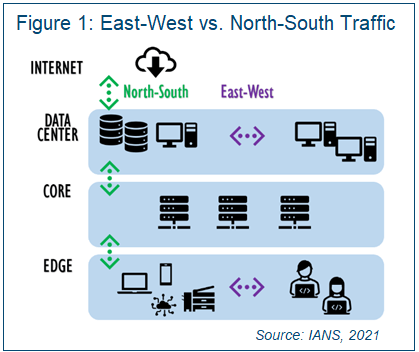
There are two types of microsegmentation:
- Data center microsegmentation: This is the granular segmentation and access rights among data center/IaaS/PaaS workloads, services or microservices.
- Network microsegmentation: This is microsegmentation that applies policies more granularly than traditional VLAN segmentation at the edge in a traditional LAN.
VLANs vs. Least Privilege Segmentation
Segmentation (in all use cases) is tricky, because best practices are highly dependent on the environment and the ability of an organization’s resources to effectively manage the access rules over time. The short answer to whether VLANs are an acceptable metric for measuring the effectiveness of any segmentation is an easy “no.”
In all cases (data center and network), segmentation should be planned based on concepts of least privilege/access. The degree or granularity of segmentation varies greatly because the enforcement methods vary greatly with products, environment and specific configuration. With VLAN-based enforcement, the number of VLANs is completely inconsequential to security posture, because most traditional segmentation methods lack an appropriate level of granularity and are often misconfigured.
Network Microsegmentation
Network segmentation can use VLANs, but that is just one of a growing number of enforcement methods, along with:
- Network functions virtualization technologies, such as virtual routing and forwarding, software-defined networking and virtual extensible LAN
- Route-based segmentation
- Internal firewall segmentation
- Purpose-built segmentation devices that take over Dynamic Host Configuration Protocol, DNS and routing functions
- Application/agent-based segmentation, such as host firewalls for network microsegmentation, which are complex because they often operate with varying effectiveness up through Layer 7
Most organizations use a combination of segmentation methods, depending on the capabilities of the endpoint and the requirements for granularity of control.
Data Center Microsegmentation
Data center microsegmentation enforcement mechanisms tend to be a bit more straightforward, because the scope is narrower. In addition to traditional software-based segmentation for physical and virtual data center services, newer solutions designed to facilitate zero trust architectures have emerged, including:
- Software-defined perimeter solutions designed to secure inbound and north-south traffic from untrusted zones.
- A host of zero trust products designed for workload microsegmentation, including servers, services and microservices architectures.
- Mileage with data center microsegmentation and zero trust products varies due to differences in product-specific support for operating systems, serverless platforms, and uni- or bidirectional requests.
Use a Risk-Based Approach to Microsegmentation
The idealistic view for microsegmentation and zero trust architectures is that each asset (whether data center- or network-based) only allows access to/from the elements required to meet business objectives, with access rights being as granular as possible (down to the port, protocol and service level vs. access to and from entire IP networks or VLANs).
The real-world implementation of microsegmentation and zero trust acknowledges that the 1-to-1 mapping of access rights to and from assets (targets) and requestors (subjects) at that level of granularity is neither practical nor sustainable for operations teams.
Instead, organizations should take a risk-based approach, identifying assets of high value and incrementally and systematically implementing controls as granularly as needed to mitigate the identified risks. A common first step is to divide classes of assets based on level of sensitivity or compliance (e.g., SOX, PCI, SOC 2, etc.) and use enclave-based models for access by authorized users and services. The controls can be tightened for more granularity and restriction as risk or needs change, and as the operations teams have the resources to manage additional workload.
Measurement of microsegmentation effectiveness in an environment is best tracked by predefined risk metrics around those assets.
DOWNLOAD: Zero Trust: A Step-by-Step Guide
Tips to Make Microsegmentation and Zero Trust Work
Organizations implementing access controls at a high level of granularity for the first time should be aware of the following:
- Product marketing literature explains the end benefit but not the mechanisms of enforcement - For network microsegmentation, most products fail to deliver on the feature promises because of product complexity or an enforcement mechanism incompatible with the environment. In data center microsegmentation, products may be limited to specific operating systems, versions and server platforms vs. others, which may address microservices and serverless architectures.
- Operational workflows change drastically when implementing more granular access rules -This means data and application owners will need to be more active participants in decision-making and implementation of controls than before. In prior workflows around access control, a designated team, such as firewall administrators, network access control administrators or similar operational groups, would create and implement access control policies based on stated requirements from an application owner. In the more dynamic and granular operations of microsegmentation, much of the workflow, including policy implementation, necessitates direct involvement from data and application owners.
- Network microsegmentation does not guarantee protection from malware and ransomware - Different products work at different levels in the Open Systems Interconnection stack, and malware variants use differing and often novel methods to perform network
discovery and lateral movement. Often, network-based controls fail to have the granularity required for malware protection once an endpoint is infected. Depending on the products and enforcement granularity in use, microsegmentation strategies may
need to incorporate additional controls, such as endpoint detection and response and other network monitoring for added protection against malware. Some microsegmentation and zero trust architecture products include these features natively or through
integration with other platforms.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in
connection with such information, opinions, or advice.