
A Strategic Guide to Maturing Your Risk Management Function
When maturing a risk management function, start by identifying value at risk in terms of data, service availability and cash. From there, map the relevant threats to exposed value—the value that matters. Last, consider the controls with the highest value (i.e., “return on control”) across those threats. This piece provides guidance to ensure your risk management program focuses on the right priorities as it grows and matures.
How a Risk Management Function Grows
Minimally, a cyber-risk management function grows in proportion to:
- Value at risk
- Relevant threats
- The state of controls
Each of these topics is covered below. Together, they create a rationale that supports growing a risk management capability.
Identify Business Value at Risk
A risk management function should grow proportionally with risk. In the book ‘How to Measure Anything in Cybersecurity Risk,’ risk is defined as “a state of uncertainty where some of the possibilities involve a loss, catastrophe or other undesirable outcome.”
What we are uncertain about is the monetizable value our businesses expose, i.e., the value at risk. For the purposes of this discussion, value at risk takes the form of:
- Data: How much regulated data do you have, what is its growth rate and how much is shared out to various third parties?
- Service availability: What are the financial impacts of downtime and/or service degradation?
- Cash: What would the impact of wire-fraud (business email compromise) and/or extortion (ransomware) be?
You cannot effectively grow your risk management function until value at risk is accurately quantified. Ironically, that means the accurate and ongoing identification of value at risk is a first area of growth.
Focus on Accuracy vs. Precision
It’s important to shoot for accuracy over precision when starting down the path of quantifying value at risk:
- Precision: We store 1,450,190 records of publicly identifiable information (PII) today.
- Accuracy: We are 90% confident the amount of PII we have is somewhere between 500,000 and 5 million records over the next year.
If the accurate range is so large as to make you overly uncertain (i.e., uncomfortable), that means you have more work to do to reduce the given range (i.e., more assessments). This same approach applies to the financial impact of business disruption (availability), as well as direct cash loss due to fraud, extortion, etc.
Quantify, qualify and then communicate about your value at risk. Oftentimes, just getting the rough magnitude of value at risk is enough to have a meaningful conversation about more capabilities. Start with broad assessments on data, downtime impact and direct cash losses for fraud and extortion. From there, you can turn to the relevant threats that would seek to compromise your value at risk.
Assess Relevant Threats
A risk management function should grow in relation to the threats that seek to compromise the value the business puts at risk. Consider ransomware. It is a threat that creates business disruption. Your systems become unavailable. This leads to not being able to conduct business. The value you create in exchange for cash is now disabled. That is why ransomware gangs can extort you.
Now, consider whether disruption of systems through ransomware would impact your ability to meet customer obligations. Perhaps it would, but perhaps it would take weeks before the business would begin to feel even the smallest financial impact from a ransomware event. (Some companies simply have minimal extortion risk as it relates to system disruption.)
As you enumerate (and weigh) the threat to loss-of-value combinations, you must consider the magnitude to which the various threats impact value at risk. For example, ransomware may not have impact due to compromising availability, but it could matter for data loss. After all, 70% of ransomware cases involve what is called “double extortion,” whereby hackers not only encrypt data stores, but they also siphon off sensitive corporate data and threaten to release it publicly. Figure 1 offers an example of relevant enumerations of value-at-risk (loss) to threats.
Figure 1: Enumerating Risks and Impacts | |
Threat | Loss |
Ransomware |
|
Business email compromise | Fraud |
Cloud compromise |
|
SaaS compromise |
|
Insider threat |
|
Advanced persistent threat (state-sponsored) |
|
Software supply chain compromise |
|
Source: IANS, 2023 | |
Quantify, qualify and then communicate about your threats in relation to value at risk. Having a very broad (accurate) understanding of your value at risk and its threats gives you deeper rationale for growth. You can understand the many-to-many relationship between these two dimensions. For example, in Figure 1, a data breach is associated with six of the seven threats deemed relevant. Of course, the question is: Just how relevant are those threats and how would we know? This leads to our final concern.
Define the State of Controls
A risk management function should grow in relation to the controls (or lack thereof) that allow threats to compromise the value the business puts at risk. Let’s start by admitting the topic of controls is large. The good news is there are ample risk frameworks to leverage. At the risk management level, it's best to think of controls as sets of capabilities or “functions.” The latter distinction is used by the NIST Cybersecurity Framework.
Capabilities should be deployed to a level necessary to protect value from relevant threats. Sticking to our ransomware example, we may want to define a set of capabilities relevant to a common vector of compromise. The example below starts with the user (other vectors can start with an exposed service) See Figure 2.
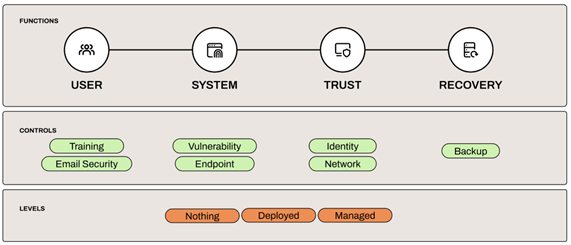
Controls line up under a functional area. For example, training and email security protect the user, while endpoint protection defends against malware that got past user controls and is now attempting to drop onto a user’s system.
You can define empirical levels of control capabilities. Perhaps “nothing” means the control does not exist, while “successfully deployed” means the control is more than 90% deployed. You could also use Sigma levels similar to what is recommended by the Center for Internet Security metrics framework. The choice is yours, but the evidence under audit must be mathematically unambiguous.
For risk management purposes, you should map “control capabilities” to relevant threats. For example, what controls map across most all threat use cases? Of those, how much impact do they have in reducing the likelihood of compromise? Are there controls that have extremely high value across all relevant threats? Are controls lacking where threats loom and the value at risk is growing? If so, it would then be your job to govern the funding, implementation and maintenance of those controls (you govern implementation and the business is responsible for execution). In this sense, risk management aligns with creating and governing security strategy.
Maturing Your Risk Management Function
Growing a risk management function without a grounding in risk is itself a high-risk proposition. It can take valuable resources away from protecting value at risk. To ensure you mature your risk management function successfully:
- Start by identifying value at risk in terms of data, service availability and cash.
- Map the relevant threats to exposed value, i.e., the value that matters.
- Consider the controls with the highest value: Determine the “return on control” across those threats.
Your program should grow to support identifying and governing the deployment of necessary controls. This evolves into a controls strategy that targets value at risk and its threats. Ultimately, risk management builds, funds and governs a strategy for
efficiently protecting business value at risk.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.