Gain Privacy Program Buy-In: Use Best Selling Leadership Points
Business leadership often views privacy programs as costly efforts with little return, but the changing regulatory environment makes a focus on privacy more imperative now than ever. The good news is the adoption of a cybersecurity framework (CSF) along with a complementary privacy framework can ease the process and gain leadership buy-in by leveraging existing processes/policies and
fostering efficiencies. This piece explains how to help leadership understand both the importance and the benefits of privacy programs.
New Privacy Rules and Data Management
A slew of new consumer privacy regulations continue to go into force. For example, the California Privacy Rights Act has gone into effect. An update to the California
Consumer Privacy Act, it provides businesses with guidance around consumer data and privacy rights. It is an effort to help consumers understand and have more control over their data. This regulation and others like it are forcing organizations to review their data collection and management processes to minimize the data they manage. They also tend to impose stricter data-sharing requirements as well. All these updated
data-handling requirements may seem daunting for an organization.
Adopt a Privacy Framework that Works
Most organizations have been building cybersecurity and data governance practices over the years, and many of these regulations’ new privacy and data-sharing requirements can be addressed by pairing existing cybersecurity frameworks with privacy frameworks and controls. In fact, much of the heavy lifting for privacy controls is already addressed in the cybersecurity safeguards.
- Example 1: The NIST CSF and NIST Privacy Framework
When you use existing cybersecurity frameworks and complementary privacy frameworks, you can merge privacy and security teams efforts, saving cycles for both.
For example, NIST published version 1.0 of the Privacy Framework on Jan. 16, 2020. It was designed to complement existing business and system development operations and to be used with the NIST Cybersecurity Framework (CSF), which was released on Feb.12, 2014. Both frameworks are built on five domains and two overlapping domains (see Figure 1).
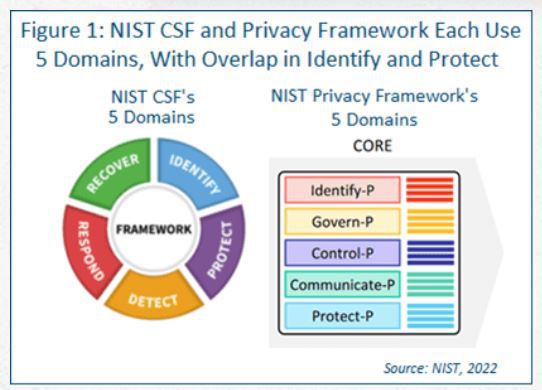
- NIST CSF and Privacy Framework Each Use 5 Domains
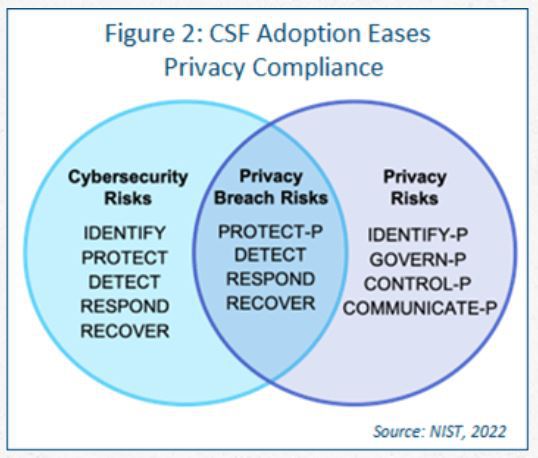
If your organization has adopted the NIST CSF, you have already implemented some of the controls in the NIST Privacy Framework. Figure 2 shows the overlap between the two cyber domains and privacy domains. As you can see, most of the heavy lifting is already done.
- Example 2: ISO/IEC 27701 and ISO 29100
ISO/IEC 27701:2019 is an international standard designed to assist organizations in creating and maintaining policies and procedures to protect data. Not only does ISO/IEC 27701 refer to building an Information Security Management System (ISMS), but it also references a Privacy Information Management System (PIMS). By running these two management systems (ISMS and PIMS) as one centralized control library, organizations can use the trusted brand strength of ISO/IEC 27701. In fact, ISO/IEC 27701 is intended to be a certifiable extension to the 27001 certifications, meaning an organization can achieve the privacy certification if they have the 27001 certifications.
The ISO 29100 Privacy Framework is another option, because it combines the privacy controls related to the EU’s GDPR into a management system.
Privacy Selling Points for Leadership Adoption
How does combining privacy and cybersecurity frameworks make privacy projects more palatable to decision-makers? By sharing a control library, organizations can:
- Use existing teams/talent to accomplish much of the privacy work: The cybersecurity team is already implementing incident response plans, logging and other activities to support the integrity, confidentiality and availability of data. Other privacy controls around reviewing, transferring, disclosing, modifying or deleting data may already be in place.
- Increase operational efficiencies: When the frameworks are combined, staffers spend less time responding to both security and privacy assessment questionnaires, leaving more time to respond to Data Subject Access Requests because personal data has already been identified.
READ: 12 Steps to Build and Improve Your Privacy Program
Benefits of CSF and Privacy Controls
If approached in the right way, privacy programs and initiatives don’t have to drain time and resources. In fact, combining a CSF with a complementary privacy control library can allow you to capitalize on continuing efforts around maturing their cybersecurity program, while also enabling you to:
- Gain customer trust: Organizations will see business gains in relationships with customers, since data collection, storage and management controls are in place and data practices are transparent.
- Field fewer customer complaints: Your customer service department can spend less time dealing with customer issues regarding data management because both you and your customers fully understand how data is handled.
- Be more confident in the organization’s ability to respond to changes in the regulatory environment.
- Obtain a competitive advantage through a better understanding of the organization’s consumer data and how it is used.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.