
Build Metrics That Resonate with Multiple Audiences
The best security metrics programs support a variety of needs, from the operational to the tactical and strategic. This piece explains how to build a metrics program that aligns with the needs of various stakeholders and helps support actionable decision-making across the business.
Develop Audience-Aligned Metrics
Organizations often struggle to establish effective security metrics programs. Threats are constantly evolving, and many teams are missing key performance indicators (KPIs) or using metrics that lack strong industry alignment. In addition, some teams present operational metrics to C-level executives and board members and are then surprised when decisions and budgetary investments get bogged down.
Elite security metrics programs align with key stakeholders (operational, tactical and strategic) to drive decisions and support actions. For this alignment to happen, however, data must be captured and presented in a way that provides the right degree of actionable information for each level.
More importantly, security metrics must be clear, concise, and easy to understand. Figure 1 explains the different features of operational, tactical, and strategic metrics.
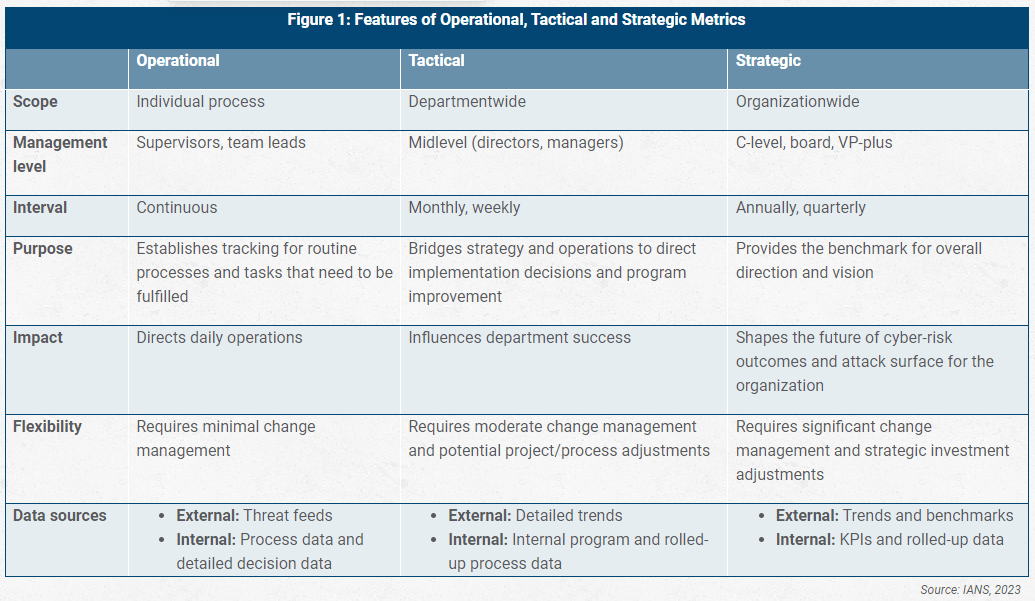
Build Operational Metrics Using the Right Tools
Data and information are critical at the operational level. Some organizations choose to match processes with tools and make reviewing these technology-specific dashboards and metrics part of the daily playbook. For example, vulnerability scanners often have dashboards and metrics built into the product.
These dashboards feature a high percentage of high-severity vulnerabilities, which may trigger a threshold for the operator to kick off a task to bring that number back in line with expectations.
Operational metrics are seldom used for strategic decision-making unless they are tied together to support a strategic outcome. In essence, they provide data that can be rolled up to support higher-level decisions.
Build Tactical Metrics Using Operational Data with Strategic Input
Program-level projects and operational health dashboards often incorporate strategy and vision at the tactical level. Strategic input, tactical metrics and reporting align to fulfill the organization’s strategy and support key decision-makers. This data often originates from:
- Program plans
- Weekly status reports
- Compliance comparisons
- Process health indicators
- Summarized operational metrics
You can find most of these metrics in systems that support security. Standard practice is to assemble a dashboard for key decision-makers, so they can engage directly with the content during their reviews. Consider creating a dashboard of dashboards (see an example in Figure 2) to make the content more easily digestible, either in a slide deck or using a data visualization tool.
The goal is to make it easy to find critical data to support tactical decisions and meet the objectives outlined in the strategy. Your tactical metrics will evolve based on staff skills, completeness of planning, threat evolution and incidents where it’s clear the existing strategy is off target and requires course correction.
Tactical-level metrics and reporting are often used during program reviews discussing project progress and security investments. It is important to approach the information through the lens of automation: How automated (manual, semi-automated or fully automated) is the process being reported on? Group the metrics accordingly.
For example, tactical metrics can highlight when a manual process needs improvement or when a semi-automated process needs to scale. Identifying these opportunities enables teams to effectively use resources and investments and address gaps in strategic funding and budgeting.
DOWNLOAD: The 2023 Security Budget Benchmark Report
Strategic Metrics: Convert Strategy into Goals
C-level executives and board members meet routinely to discuss organization wide performance against strategic milestones—often once a quarter and centered around investment decisions. To align with this practice, consider converting the organization’s security strategy into top-level goals, with defined investments and KPIs.
Also, consider presenting the data in the same manner (summaries, format, etc.) as other departments. If this isn’t possible, try to use a consistent, durable format that can be replicated, regardless of the security process.
At the executive and board levels, strategy is commonly translated into organization-wide improvements with health metrics to demonstrate progress. This is not necessarily standard practice for security, however, reporting to the board is still quite new and we are still working out the best methods to standardize content.
That said, it’s important to consider how boards consume content:
Information is usually conveyed in a slide deck, so the board can pre-read the deck before the formal discussion.
- Formal change management for any content is often standard practice, so it is important to review all changes with senior management to make sure the purpose is clear and everyone understands the content.
- It is standard practice to color code (e.g., green/yellow/red) KPI status and identify if anything is off track or requires action. You might also include a linked slide offering tactical planning for intended actions.
- Be sure to keep it simple and easy to read. Summarize tactical and operational information and avoid speaking in security acronyms executives and board members may not be familiar with.
Tips to Build a Strong Metrics Program
As you align your metrics, consider the following steps:
- Look to industry-specific content guides, such as the Center for Internet Security Measures and Metrics or compliance standards, such as PCI DSS. Use these to guide reporting and metrics requirements during the procurement process and provide feedback on needed features.
- Assemble an organization-wide cybersecurity metrics catalog. This can be very helpful for finding opportunities to refine processes and increase risk reduction across the organization.
- Set expectations with vendors to address metrics and reporting requirements. Holding vendors accountable for operational reporting is critical to the success of a cybersecurity program.
Download our Security Budget Benchmark Report
Each year, IANS, in partnership with Artico Search, releases a series of benchmark reports on CISO compensation, security budgets, organizational design, staff compensation, and job satisfaction.
These in-depth reports feature new takeaways, uncover a wealth of insights, and provide valuable leadership guidance to fine-tune your current role, department, and career path.
Download our Security Budget Benchmark Report – the first in our CISO Comp and Budget Report series – and gain access to key budgetary data and other valuable insights helpful to gain security investment buy-in.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.