
Guidance for CISOs Presenting to the C-Suite
For CISOs presenting security metrics to the C-suite, we suggest focusing on three main metrics: high-level stats that get attention, framework-based stats that provide assurance and finer-grained data that demonstrates rigor. This piece provides security leaders with recommendations on how to use those three tips to provide executives and board members with the insights necessary to make strong risk management decisions.
Three Tips for CISOs Presenting to the C-Suite
For CISOs and other security leaders presenting to the C-suite, we recommend starting high-level and qualitative, and then drilling down into empirical measurements. Consider the following three tips:
- Get attention: Connect the world to your headline.
- Provide assurance: Build trust with third-party frameworks.
- Demonstrate rigor: Use core capabilities metrics over time.
Tip 1: Get Attention
Board members do care about security, and they will tell you they do. However, when you walk into the room, you need to draw them into your material – into your headline to ensure you have their focus and attention. A good way to try and do that is to connect to something relevant. Consider leading with something that already occupies a part of their attention, such as recent threats in the news.
Take the SolarWinds breach. Board members are all over this. Most have generalized it to broader supply chain attacks. The topic of supply chain security brings in a myriad of cyber risk topics, like assurance (vulnerabilities/configurations), third-party risk management (public cloud, etc.), software development lifecycle (SDLC) and more. Boards (if not already) will likely be leaning into this topic with the CISOs. Supply chain is becoming the new No. 1 cyber risk driving budgets. For right or wrong, this is how it works.
From a metrics perspective, then, you can consider listing out both the capabilities relevant to this threat and those at risk in your organization. These measures should be more qualitative. They are meant to be drilled into. It’s here where you would want to connect to the next level of metrics.
GET STARTED: CISO Compensation & Budget Benchmark Survey
Tip 2: Provide Assurance
For better or worse, your board and peer executives need constant assurance. With the first set of metrics, you have demonstrated you are thinking about threats. You have shown how those threats are relevant to your program and its capabilities, and you have shown where there are opportunities for improvement.
Now, consider talking about your internal capabilities and connect them to an outside perspective. This is where you can build trust by using a framework supported by an outside authority. A suggested go-to is the NIST Cybersecurity Framework (CSF).
The NIST CSF is organized around five macro capability areas: identify, protect, detect, respond, and recover. It also provides several tiers or maturity levels (the CSF tries to make a case for the tiers not being maturity levels – but then goes on to lay out how you use them to that very end).
You can make a case for supply chain assurance cutting across all the functions. For example:
- Identify has sub-capabilities like asset management, identity and access management (IAM) and more.
- Protect has sub-capabilities like vulnerability management and SDLC, etc.
- Detect has sub-capabilities like SIEM, etc.
Decompose each of the five capabilities into key “measurable” sub-capabilities, like the bullets above. Then assign measurement achievements, or key performance indicators (KPIs), for each sub-capability based on the CSF tiers.
Figure 1 below shows an example with just three of the NST CSF functions (protect, detect, respond) with modern sub-categories under each.
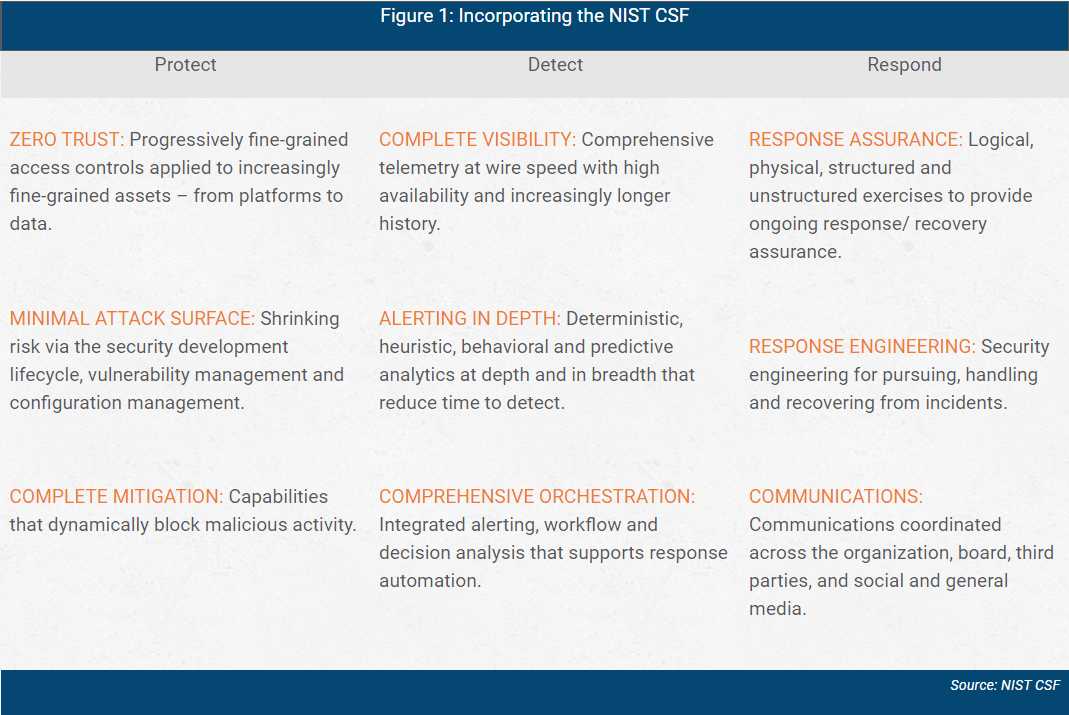
The KPI is a measurement that represents the tier of maturity you have achieved within that sub-category. For example, one of the maturity KPIs for vulnerability management (within CSF’s protect area) could be 90 percent scan coverage. You would
also likely have KPIs for remediation efficiency and more.
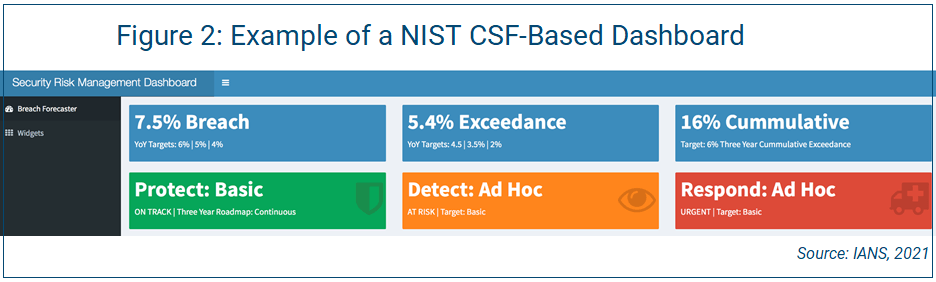
Figure 2 shows a portion of a NIST CSF-based dashboard that incorporates the categories in Figure 1.
Tip 3: Demonstrate Rigor
Each KPI has more detailed metrics that support it, and that’s where you can demonstrate rigor. However, if detailed metrics are included in a board presentation, they should be in an appendix. Most board-level conversations happen at the framework (assurance) level, not the detailed metric level.
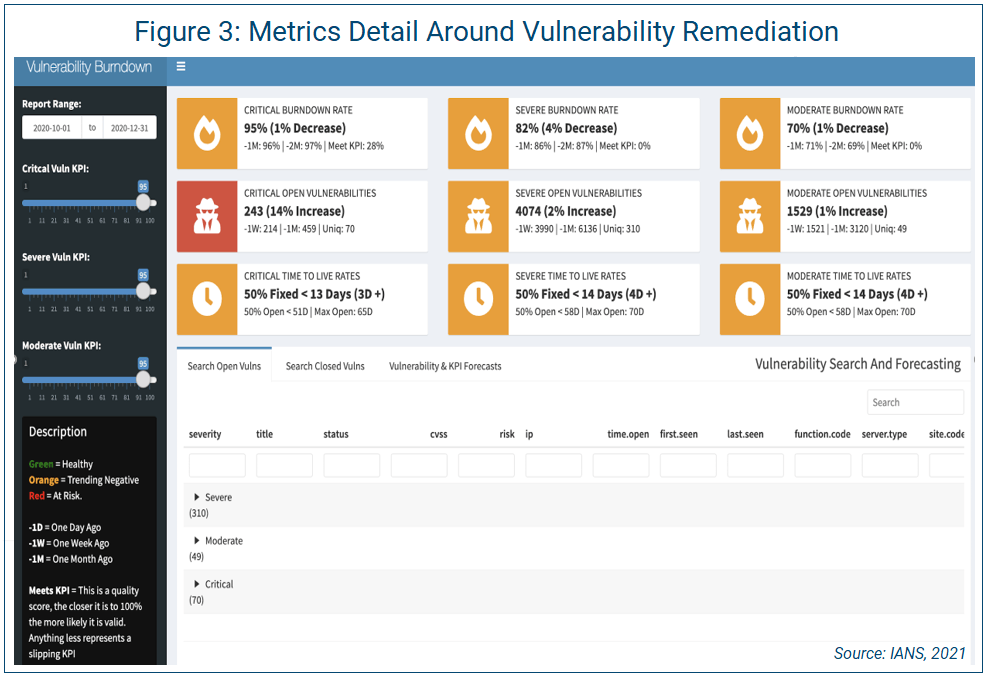
For example, the CSF function of “protect” has the sub-category of “vulnerability management.” Vulnerability management has KPIs around “coverage” and “remediation management” and more. Figure 3 on shows an example of metrics detail for remediation management (burndown).
Advice for CISOs Presenting to Executives
When CISOs are presenting information security metrics to the board or other C-level executives, it’s important to keep the three categories of metrics front and center:
- Get your listeners attention. Use what is in the news, even if its months old, to draw them in. Then, connect that material to your capabilities.
- From there, drop into a regulatory framework. This provides assurance and guidance. The achievement of requirements in the framework should be demonstrated via KPIs.
- Don’t get hung up on the minutia. The KPIs should all have detailed metrics beneath them, but you should only show that level of detail as needed (and most likely in an appendix).
RELATED CONTENT: How Information Security Leaders Can Engage the Board Effectively
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.