
Who Should the CISO Report To?
A wide variety of reporting structures can work if the CISO is understood to be semi-independent and governed by a group of trusted business, regional and functional leaders. This piece outlines the pros and cons of typical CISO reporting structures and
offers tips for pursuing the right balance for the organization.
State of CISO Reporting Structure
As a relatively new discipline, information security does not have a strong established reporting structure. Because infosec generally emerged from IT, the majority of CISOs today report into the CIO. However, the CISO organization has many different
possible anchor points and thus many paths to the successful protection of information and information assets. CISO reporting structures depend on many factors, including organizational history, circumstance, personalities, and risk maturity. There
is no single “right” reporting relation.
The most productive way to think about this is to frame the discussions in terms of where the CISO can most effectively lead the organization to avoid circumstances that might lead to harm. When considering security frameworks like the NIST Cyber Security Framework, we can further detail effectiveness in terms of identify, protect, detect, respond and recover.
GET STARTED: CISO Compensation & Budget Benchmark Survey
Evolution of CISO Reporting Structure
Over the past decade, information security has kept its roots in technology, but expanded to include semi-independent and trusted oversight of people, processes and technology to assure protection of confidentiality, integrity and availability (CIA) of information and information assets, whether digital or otherwise. This came about as organizations realized security is not just a technical problem. As threats emerge, information security must often take ownership of major behavioral change initiatives, such as anti-phishing campaigns, social engineering avoidance, managing executive social media exposure, etc. Sometimes, being perceived as part of IT detracts from the CISO’s effectiveness in governing non-IT aspects of security.
First-Party Survey Data on CISO Reporting Structure
In our 2020 CISO Compensation and Budget Survey, 66% of CISOs said they report to a technical function—a CIO, CTO.
However, in 2021, this share grew slightly year-over-year to 69%. Eighteen percent of survey respondents reports to the CEO or chief operating officer (COO) and only a small share has a chief risk officer (CRO), chief financial officer (CFO) or general counsel as their solid line manager (see figure below).
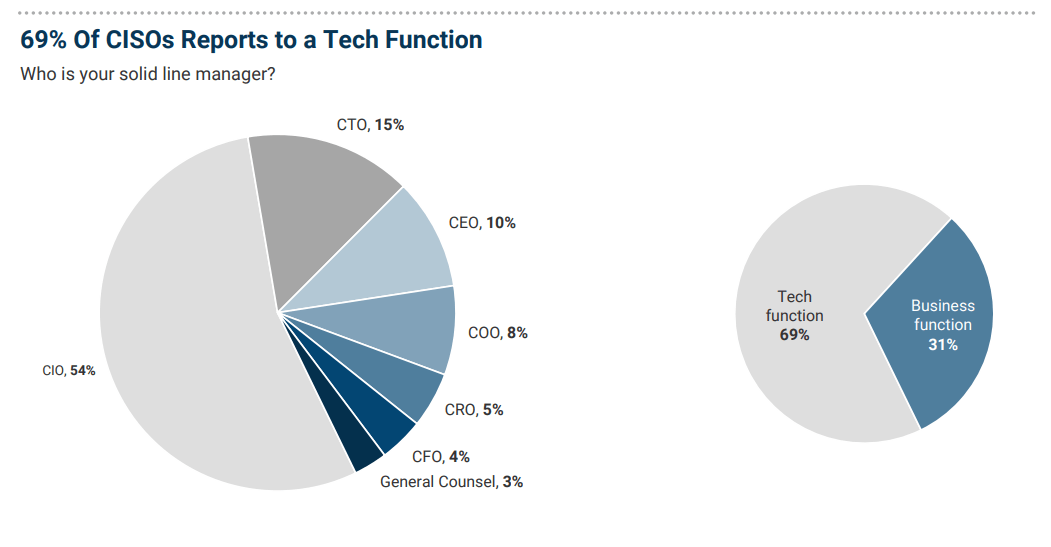
Source: IANS + Artico CISO Compensation & Budget Survey
According to Steve Martano, cybersecurity recruiter at Artico Search, this trend is remarkable, "because there can be an inherent conflict of interest between security and IT, for several years we have heard from organizations that security would break out of IT and become a separate function reporting to a business executive, but that has not really come to fruition yet. For now, the CISO predominantly reports into the tech group, but we have seen it work in a variety of ways, depending on the organization and individual leaders in other functions."
The typical stages in the evolution of the CISO position are:
- A few folks specializing in security within IT operations.
- A recognized IT security sub-group that spans operations, applications, policy, compliance, governance, etc., and reports to a security IT manager/director.
- An IT executive elevated to CISO under the CIO. With this elevation and additional data strategy role, the CISO sometimes transforms into the chief data officer (CDO).
- A company executive or senior executive reporting in parallel to the CIO – often both to the chief financial officer (CFO) or chief operating officer (COO), but sometimes under a newly empowered CRO.
- A senior executive CISO reporting to the CEO on the executive leadership team. This happens primarily when information security is viewed as critical to company success.
There is no standard reporting hierarchy. The actual path taken differs by industry and company circumstance. The degree of government regulation and public scrutiny also shapes the reporting structure.
Determine Who The CISO Reports To
The following are key attributes organizations should consider using to determine who the CISO should report to and overall structure of the information security function:
- Independence: Is the CISO free to give honest, unbiased, clear evaluation and guidance? Is the CISO positioned to be able to report and influence all levels of leaders without undue conflict-of-interest pressure?
- Governance: Is the CISO guided by a trusted core of key business, region and functional leaders? Is the security program owned by them and not just the CISO?
- Impact: Is information security positioned to be successful in its operational components (e.g., identity and access management, firewall management)?
- Influence: Is the CISO positioned to be a strong partner (not policeman) with all business, regional and functional leaders as well as outside entities (e.g., customers, the board, regulators, etc.)?
- Resolve: Can the CISO engage and lead the necessary difficult conversations to find a way forward by balancing the tensions among business, security, regulation and stakeholder expectation with regard to mitigating circumstances and minimizing harm?
Additional CISO Reporting Considerations
The advantage of reporting into IT is that everyone is accustomed to IT’s large budgets and programs. IT also generally has the resources to manage the budget process and do project management. Those roles may be hard to find in other areas of the
organization. For example, they will require significant time and resources if the CISO reports directly to the CEO or to a functional organization that is not used to this scale (e.g., the chief legal officer). The budget/program advantage must be
balanced against the IT-only perception disadvantage.
Try to Achieve an Optimal Balance
Use the CISO success factors to understand the specific drivers for CISO reporting in your organization. A wide variety of reporting structures can work if the CISO is understood to be semi-independent and governed by a group of trusted business, regional
and functional leaders.
Things to Avoid
- Being perceived as an IT problem. Reporting into IT with limited ability to influence the behavior of employees, partners and suppliers won’t lead to success. Also, this positioning can be used to exclude the CISO from the protection of non-IT technology (e.g., shadow IT) and non-digital assets (e.g., paper records, staff disclosure of secrets, etc.).
- Being perceived as the policer of the organization. Act as the mirror and window, not just the locked door. In other words, strive to clearly present risks and instead of simply banning new initiatives, offer innovative solutions that mitigate risk while enabling the business.
- Reducing your role to a checklist of compliance points that are static and often can never be satisfied. Focus on risk management and business decision-making.
- Having your hands tied. Avoid a reporting relationship that does not provide you, as CISO, with the ability to raise awareness of risks to whatever level of leadership is appropriate to stimulate action to address those risks. In a boss, seek mentorship,
not “must be approved by me” filtering.
Things to Seek
- A good network of leadership mentors to help you understand how to bring about change. Establish trust with your boss as a key member of your mentor group.
- Understanding of your own leadership maturity with an eye toward growing your skills. Sometimes, this means reporting further down in the organization with an understanding that as you develop, your reporting will move upward.
- The freedom to engage in difficult conversations where you can elaborate the risk clearly and take a personal position, but understand the decision to accept, mitigate or transfer that risk is up to business leadership, not IT or information security.
- A strong trust relationship with the CIO and IT leadership, so you can develop your programs and budgets in collaboration. The rest of the organization will perceive IT plus information security as a combined cost of doing business, so it is best to resolve
tradeoffs directly between the CIO and CISO. Pay attention to and benchmark the budget ratios, such as:
- IT to revenue
- Infosec to revenue
- Infosec to IT
- Infosec to research and development (R&D), etc.
- A healthy challenge-collaborate environment, not a conflict-adversary environment.
Finally, CISOs must do an honest appraisal of the risk maturity of the organization and of their own ability to interact at the highest levels of leadership in the organization. Seek mentor input on your conclusions. Plan your growth and negotiate for a reporting relationship that leads you to the next level of maturity and, possibly, a later revision of your reporting structure. Be humble and focus on your core mission and principles.
READ: How to Structure the Information Security Function
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.