Get the Latest Report on How CISOs Are Leveraging AI in 2026
AI Heading Into 2026: CISOs See Change, Growth and Opportunity
Access objective, data-driven insights from IANS community polls and hard-won lessons from CISOs who are actively implementing AI in their organizations. Download this report to understand:
- The evolving standards shaping AI policy and governance, and how CISOs are tightening access while building business-aligned oversight.
- How leaders are redefining AI vendor strategy, moving to multi-vendor models with stronger guardrails for data and operational risk.
- The top AI-driven priorities commanding executive focus in 2026, from workforces augmentation to identity assurance and AI-enabled threats.
Download the report to benchmark your AI strategy against real-world CISO practices and stay ahead of emerging risks.
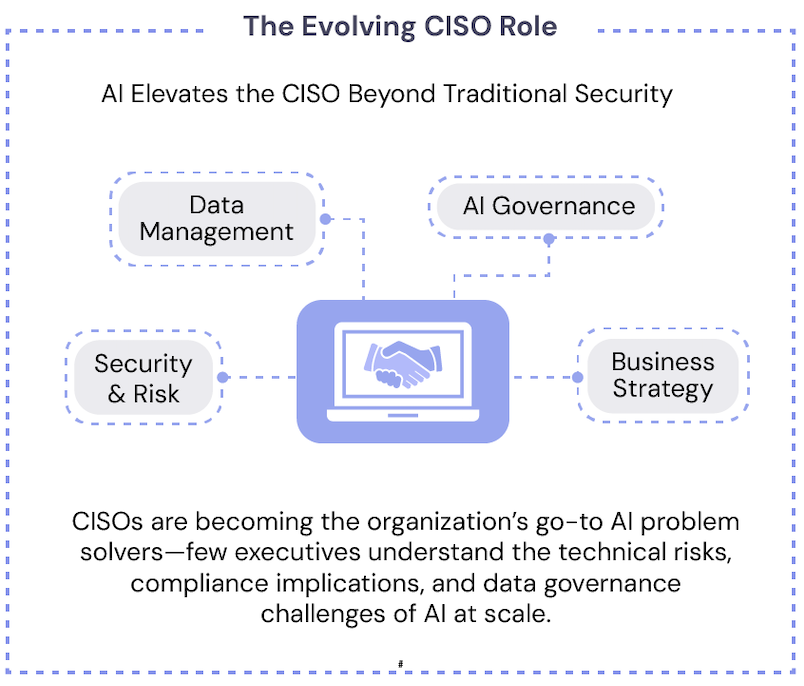
CISOs Lead the AI Governance Challenge
The 2026 AI Report combines data from IANS community polls with hard won lessons from CISOs on the front lines of AI adoption.
Start by reviewing the insights in the infographic, then download the Report to uncover what these developments mean for today's security leaders.
What's the REAL Risk of Autonomy in AI Agents Today?
Many leaders dream of fully autonomous agents that can replace or augment staff. But the hard truth is: autonomy and control exist on opposite ends of a scale. In this video, Jake Williams, IANS Faculty, breaks down one of the biggest misconceptions about deploying Agentic AI.
Your employees want to use generative AI tools, especially chatbots. If you don't provide access to vetted and approved tools, employees will find ways to expose your data to unapproved tools.

The CISO's Expanding AI Mandate: Leading Governance in 2026
CISOs find themselves at an inflection point in 2026. They are no longer simply gatekeepers of cybersecurity; CISOs are emerging as leaders of AI governance across their organizations. This evolution is redefining what it means to be a security executive in 2026.
Additional Resources
Prompts for Testing AI Security

Mitigate These Five AI Risks

Securing Microsoft 365 Copilot: A Checklist (Updated)

Prepare for Recursive AI Cryptographic Attacks

AI Acceptable Use Policy Template
.png?sfvrsn=e4b46d1f_2)